An In-Depth Look at Pandora Ransomware
Executive Summary OF Pandora ransomware
In March 2022, it was discovered that the Pandora ransomware group was targeting high-profile victims on their leak site. Five victims have been posted on the site since February 2022 and that number appears to be growing. The threat actor is responsible for compromising the network of the second-largest automotive parts supplier in the world - Denso Corp.
In February 2022, CISA, the FBI, and the NSA released a joint advisory concerning ransomware trends from 2021. The advisory stated that although ransomware was a hot topic in 2021, attacks were expected to increase in 2022. According to the advisory, the top trends outlined include:
- Ransomware groups increasingly targeting organizations on holidays and weekends (Denso Corp. was compromised on a Saturday)
- Cybercriminals are increasingly gaining access to networks via phishing, stolen Remote Desktop Protocols (RDP) credentials or brute force, and exploiting software vulnerabilities.
- The market for ransomware became increasingly “professional” and there has been an increase in cybercriminal services-for-hire.
- More and more, ransomware groups are sharing victim information with each other, including access to victims’ networks. (Pandora may be connected to another ransomware gang)
- Cybercriminals are diversifying their approaches to extorting money.
- Ransomware groups are having an increasing impact thanks to approaches targeting the cloud, managed service providers, industrial processes, and the software supply chain. – gov
Last year, many had ransomware fatigue and there was always a new ransomware operation taking center stage (Conti, LockBit 2.0, BlackMatter, etc.). However, as we end the first quarter of the year and move toward the second, it’s important to keep watch over ransomware threat actors even if they’re constantly being discussed. As you can see from the above list, ransomware operations are constantly evolving and will continue to do so throughout 2022. Let’s take a look at Pandora ransomware, their tactics, as well as their techniques.
pandora ransomware and denso corp.
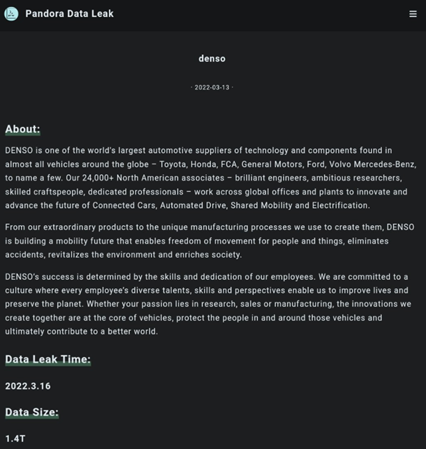
On March 10, 2022, the Pandora ransomware gang successfully compromised the networks of a major automotive parts supplier, Denso Corp., a Japanese-based company. Denso Corp. is a multibillion-dollar supplier to automotive companies such as Mercedes-Benz, Toyota, Honda, Volvo, and Ford.
The attack took place on a Saturday at a company office in Germany and threat actors stole sensitive data, posting it on their data leak site. According to Denso Corp., their networks were “illegally accessed” by Pandora and they promptly cut off the network connection of devices that received unauthorized access. See their statement regarding the breach below.
“DENSO has confirmed that its group company in Germany network was illegally accessed by a third party on March 10, 2022. After detecting the unauthorized access, DENSO promptly cut off the network connection of devices that received unauthorized access and confirmed that there is no impact on other DENSO facilities. Details are under investigation, there is no interruption to production activities. The company keeps operating its all plants as usual.
DENSO has already reported this incident to the local investigative authorities. The company is working with them and specialized cyber security agencies to deal with this situation.
DENSO would like to express its sincerest apologies for any concern or inconvenience resulting from this incident. Denso Group will once again strengthen security measures and work to prevent a recurrence.” - DENSO.com
As we stated, Denso is a large automotive parts supplier and reported a revenue of $44.6 billion last year. They also have more than 200 subsidiaries and over 168,000 employees worldwide – an appealing target for a ransomware gang.
Image 1: Pandora's Message About Denso Corp. Breach
After attacking Denso Corp., Pandora leaked 1.4 terabytes (more than 157,000 items) of stolen data belonging to Toyota Motor Group – making it the second time in weeks that Toyota had been compromised. The March 2022 data leaked included emails, purchase orders, non-disclosure agreements, technical drawings, and other classified information. Previously, Toyota had to shut down 14 plants in February 2022 after they experienced a “supplier system failure”. Cyber security professionals believe that the company was the victim of a cyber attack, but Toyota did not confirm an attack. The alleged attack impacted Toyota supplier, Kojima Industries Corp.
Source: Twitter.com/darktracer_int
According to ThreatPost, the attack came on the heels of Japan rejoining Western allies in blocking Russian banks from accessing the SWIFT international payment system and committing to giving Ukraine $100 million in emergency aid. Kojima, a Japanese auto parts supplier and member of the Toyota Group, supplies parts and electronic components to Toyota.
PANDORA'S tactics, techniques, and infection process
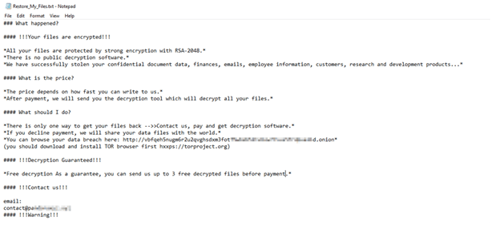
In March 2022, Cyble Research Labs conducted an in-depth analysis of Pandora ransomware and published their findings. Pandora ransomware infects and locks files so that you cannot open them - before leaving a ransom note directing you to contact them for the decryption key. Cyble discovered that the file encrypts the victim’s systems and drops a ransomware note into each folder named “Restore_My_Files.txt.” after execution. Once encrypted, the file is renamed with the “.Pandora” extension.
A decryption loop is run by Pandora, which decrypts the strings present in the file. After the loop is run and strings are decrypted, the malware creates a mutex named “ThisisMutexa” by using CreateMutexA() API. This ensures that only one instance of malware is running on the system. Pandora evades anti-virus detection by disabling the Event Tracing for Windows via patching the EtwEventWrite() function, which further bypasses the Antimalware Scan Interface.
Before encryption, Pandora checks and excludes some folders from being encrypted. Those folders include Google, AppData, Windows Windows.old, Tor Browser, Internet Explorer, Opera, Mozilla, Program Files, Boot, ProgramData, Program Files (x86), and Opera Software. By way of the UPX packer, Pandora is packed and after unpacking, the payload is compiled using Visual C++. Because the file has encrypted strings, jumps, and calls, this can make debugging difficult.
Autorun.inf, boot.ini, bootfont.bin, bootsect.bak, bootmgr, bootmgr.efi, bootmgfw.efi, desktop.ini, iconcache.db, ntldr, and ntuser.dat are also excluded from encryption. Pandora also deletes shadow copies u using ShellExecuteW() API. Pandora searches for files using: FindNextFileW () and FindFirstFileW().
It appears that the above exclusions are related to OS, user, or browser processes - except iconcach.db, which is used to store copies of the icons used by shortcuts. Pandora may need iconcach.db for their ransom note shortcut.
Multithreading is used for faster encryption, using: CreateThread(), SetThreadAffinityMask(), ResumeThread(), CreteIOCompletionPort() and GetQueuedCompletionStatus() APIs. Exempted from encryption are the following extensions: .pandora, .hta, .exe, .dll, .cpl, .ini, .cab, .cur, .drv, .hlp, .icl, .icns, .ico, .idx, .sys, .spl, and .ocx. After the above steps, Pandora leaves a ransomware note.
Image 2: Ransomware Note Left by Pandora
Source: Cyble.com
According to Malware Warrior, Pandora uses double extortion to blackmail their victims into paying their desired ransom. The ransomware encrypts sensitive files to restrict keep their victims from being able to open their files. The ransom note left behind, claims that they will delete the decryption key and refuse to give you access to your stolen files if you refuse to pay their ransom. Pandora is a new ransomware strand, so it’s unknown how threat actors breached Denso Corp. to infect their network. How much Pandora is trying to extort out of its victims is also unknown.
Bridgestone attack – Before the denso corp. attack
Also, in March 2022, Bridgestone Corp. notified the public that they were hit by a ransomware attack. Bridgestone is a tire supplier for Toyota vehicles. Initially, it was suspected that Pandora was behind the attack because it happened shortly after the gang attacked Denso Corp., however, it turned out to be the work of LockBit ransomware. Earlier, we mentioned that threat actors are getting crafty in their attacks and some groups are sharing information with one another, therefore there is still a possibility of a relation between LockBit and Pandora.
In February 2021, Bridgestone told ThreatPost that they detected an IT security incident on February 27, 2022. The company stated that they notified federal law enforcement upon their discovery and stayed in communication with them. Bridgestone’s breach impacted several cities and plants were inoperable for days. LockBit gave Bridgestone a timeframe to pay their demanded ransom before they released the company’s data. Like other ransomware groups, LockBit removed information from Bridgestone’s systems and threatened to disclose the information to the public. Bridgestone was the second auto parts supplier attacked by a ransomware gang in a very short span of time.
relationship to rook ransomware & suspected re-brand
In December 2021, Denso Corp. was named on the victim list of a leak site by the ransomware gang ROOK. During the same month, ROOK claimed to be responsible for attacking one of the largest automotive suppliers of technology and components, as well as Kazakhstan-based financial institutions. Rook is delivered by a third-party framework (i.e., Cobalt Strike) and phishing emails. Like Pandora, ROOK’s samples are UPX packed.
After ROOK named Denso Corp. as a victim, their leak site went dark at the end of January 2022. Pandora ransomware was launched shortly after and posted Denso Corp. as a victim on their leak site in March 2022. Due to their similarities in tactics and technics, as well as how they operate, it is suspected by Cyble that Pandora is a re-brand of ROOK.
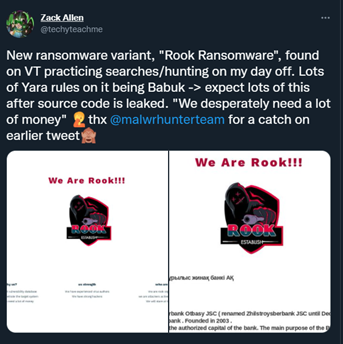 Image 3: Tweet About Babuk and ROOK
Image 3: Tweet About Babuk and ROOK
According to CPO Magazine, ROOK and Pandora share code similarities. Also, VirusTotal (Google’s virus detection) detects Pandora as ROOK, derived from Babuk ransomware, which is based on a leaked source code. The ROOK ransomware variant was suspected of being Babuk’s latest spawn because a set of YARA rules associated with ROOK, came from Babuk. Additionally, the analysis from Virus Total stated that the code is a generic Babuk ransomware code. Babuk is now a defunct ransomware-as-a-service
Source: Twitter.com
manufacturer supply chain attacks
Although the global supply chain has enabled manufacturers to be economical, this makes them easy targets for ransomware attacks. Because supplies are delivered on a consistent basis, plants perform “just-in-time” production – reducing wasted time and inventory expenses. Toyota invented this kind of operating philosophy, but it may have come back to haunt them.
Since COVID-19, there have been demonstrated risks of “just-in-time” production. When a ransomware gang compromises a company that operates with a philosophy of choreographed processes and is interrupted by an IT shutdown, the consequences are felt far and wide. Organizations being efficient in their ransomware responses is just as important as being efficient in daily operations.
In 2021, Security Intelligence conducted a study and found that 21% of ransomware attacks happen against manufacturing. In the manufacturing industry, every minute of inactivity costs money. This is appealing to ransomware gangs because they know disrupting work in places with high pressure, leads to ransom payments.
Relying on digital supply chain solutions increases supply chain attacks. Although relying on digital systems is unavoidable, it’s time for organizations and companies to start protecting themselves from these attacks. We don’t know all the details regarding how Denso Corp. was breached, but here are a few tips on how your organization can remain safe in general:
- Implement email security software as a part of your organization’s defensive strategy. This helps with email-based supply chain attacks.
- Guard against supply chain IP theft. Third parties in your supply chain could abuse their access to intellectual property or other sensitive data.
- Protect against threats that could interfere with the products you create by conducting thorough due diligence. Be sure to document and identify supply chain partners via quality assurance.
- Do not make data accessible to unauthorized third parties.
- Always practice cyber security best practices across your organization – this includes third parties. Make sure that third parties follow cyber security best practices just as your organization would follow them.
How Avertium is Protecting Our CUSTOMERS
- Avertium recommends utilizing our service for DFIR (Digital Forensics and Incident Response) to help you rapidly assess, contain, eradicate, and recover from a security incident like a cryptomining malware attack.
- Implement XDR as a prevention method. Our XDR is a combination of monitoring software like LogRhythm, Microsoft Azure Sentinel, or AlienVault, combined with endpoint protection such as SentinelOne. XDR platforms enable cybersecurity through a technology focus by collecting, correlating, and analyzing event data from any source on the network. This includes endpoints, applications, network devices, and user interactions.
- Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
- Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A Security Information and Event Management (SIEM) system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior.
- Avertium offers third-party risk monitoring and attack surface management.
Avertium’s Recommendations – PROTECT AGAINST PANDORA RANSOMWARE
- Prioritize your cyber asset management strategy and discover all cyber assets in your IT environment.
- Clearly understand your cyber asset inventory and security coverage gaps in order for security controls to work effectively.
- If infected by Pandora ransomware, isolate the infected device and disconnect from the internet. Follow this step by unplugging all storage devices to prevent corruption.
- Always ensure data backups are running properly - this should be done consistently to help prevent loss of data if your organization is ever compromised.
- Review your organization’s operational policies to limit supply chain risk.
MITRE TTPs
- [T1195] Supply Chain Compromise
- [002] Supply Chain Compromise: Compromise Software Supply Chain
- [T1509] Command and Scripting Interpreter
- [T1082] System Information Discovery
- [T1486] Data Encrypted for Impact
- [T1490] Inhibit System Recovery
- [T1083] File and Directory Discovery
Indicators of Compromise (IoCs)
- settings-win-dyndns-office[.com]
- http://ns162.nsakadns.com:443/api/v2[/ajax]
- https://89.35.178.105:443/api/v2[/ajax]
- http://35.187.148.253:443/api/v2[/ajax]
- http://85.204.74.143:443[/ajax]
- http://47.75.49.32:443/api/v2[/ajax]
- http://35.220.135.85:443/api/v2[/ajax]
- http://139.180.208.225:443[/ajax]
- 0c4a84b66832a08dccc42b478d9d5e1b 160320b920a5ef22ac17b48146152ffbef60461f
- 5b56c5d86347e164c6e571c86dbf5b1535eae6b979fede6ed66b01e79ea33b7b
Supporting Documentation
CISA, FBI, NSA and International Partners Issue Advisory on Ransomware Trends from 2021 | CISA
Pandora Ransomware Hits Giant Automotive Supplier Denso | Threatpost
Rook Uses Babuk's Leaked Code in Kazakh Bank Attacks (bankinfosecurity.com)
Cyble — Deep Dive Analysis – Pandora Ransomware
2021 Manufacturing and Supply Chain Security Roundup (securityintelligence.com)
Software Supply Chain Attacks more than tripled in 2021 (aquasec.com)
How to remove Pandora ransomware — Malware Warrior
Pandora Ransomware Removal - Decrypt Pandora Ransomware - EasySolveMalware.com
Notice of Unauthorized Access to Group Company | Newsroom | News | DENSO Global Website
Toyota to Close Japan Plants After Suspected Cyberattack | Threatpost
Kojima Industries Corporation - MarkLines Automotive Industry Portal
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.
Related Resource: [Threat Report] An In-Depth Look at Conti's Leaked Log Chats