Ransomware Groups Pivoting Away from Encryption
executive summary
In recent years, ransomware groups have been evolving their tactics and moving away from the traditional strategy of encrypting victims’ data and demanding ransom for decryption keys. Instead, many ransomware groups are now shifting their focus towards data extortion.
This shift represents a significant departure from their previous methodology and poses a more significant threat to businesses and individuals. Rather than merely locking access to data, ransomware gangs are now exfiltrating sensitive information before encrypting it, leveraging the fear of data exposure to exert pressure on victims. It's important to note that threat actors still demand a ransom; however, their primary focus has shifted away from encrypting data. Let's examine ransomware groups that have shifted their focus towards data extortion and explore the reasons behind this strategic change.
tir snapshot
- When ransomware groups skip the encryption process and go straight for exfiltrating data and holding it ransom, it's called data extortion.
- The threat of data exposure multiplies the pressures on victims. Ransomware groups understand that the potential consequences of data leaks, such as reputational damage, regulatory fines, and legal liabilities, far outweigh the cost of the ransom.
- One of the most recent ransom group's moving towards data extortion is 8Base. This group evaded detection for over a year before resurfacing with an alarming surge in operations during May and June 2023.
- 8Base's most recent attack targeted the Canadian provincial government entity, Alberta Dental Service Corp. Despite the dental organization having backups and the ability to restore services, the data of 1.47 million individuals, including personal banking information, was compromised.
- Emerging in August 2022, BianLian gained notoriety as a ransomware strain capable of swiftly encrypting files.
- BianLian switched to extortion-based data theft without encrypting systems in 2023.
- In BianLian's latest attack, the group targeted one of the world's oldest and largest charities, Save the Children, stealing nearly 7TB of data including financial, human resources, personal, and medical information.
- Instances of data theft and extortion without any data encryption or ransomware usage increased by 25% from April 1 to the close of June 2023. These cases constituted 30% of the incidents to which the organization resonded.
- There are several reasons why threat actors are starting to pivot from encryption to data extortion, with increased profitability being the main factor. An organization's focus should revolve around fortifying systems and networks against unauthorized threat actors.
data extortion
When ransomware groups skip the encryption process and go straight for exfiltrating data and holding it ransom, it's called data extortion. In the past, Avertium discussed data extortion in published Threat Intelligence Reports; however, some may still be unclear on how it works. Lately, ransomware groups like Karakurt have been bypassing encryption and focusing on stealing data instead.
The threat actors do this by infiltrating a company's network and stealing valuable data, such as customer information, intellectual property, or confidential emails. Instead of solely locking access to the data through encryption, the threat actors threaten to expose the stolen information to the public or sell it on the dark web if their demanded ransom is not paid.
The threat of data exposure multiplies the pressure for victims. Ransomware groups understand that the potential consequences of data leaks, such as reputational damage, regulatory fines, and legal liabilities, far outweigh the cost of the ransom. Some ransomware groups (such as 8Base) employ a double-extortion strategy, demanding payment for both the decryption key and the assurance that stolen data won't be exposed. This approach maximizes their chances of receiving a ransom payment.
recent attacks
8BASE
One of the most recent ransomware group’s moving towards data extortion is 8Base. This group evaded detection for over a year before resurfacing with an alarming surge in operations during May and June 2023. 8Base has been in operation since 2022 and has targeted more than 67 entities, with a focus on the manufacturing, construction, and business services sectors in the U.S. and in Brazil.
In June 2023, 8Base's methods took a more aggressive turn, using a double extortion strategy to compel victims to meet their ransom demands. Although potentially associated with the notorious RansomHouse group, the origins of 8Base remain shrouded in uncertainty. Nevertheless, their effective operations and preference for targeting smaller businesses give rise to significant cybersecurity concerns.
8Base's most recent attack targeted the Canadian provincial government entity, Alberta Dental Service Corp. Despite the dental organization having backups and the ability to restore services, the data of 1.47 million individuals, including personal banking information, was compromised. Alberta Dental Service Corp. ultimately paid the group's undisclosed ransom demand, and in response, 8Base provided evidence that the stolen data had been deleted. Nevertheless, like all cybercriminal groups, an organization can never be absolutely certain that all the stolen data was deleted and will not be leaked.
BIANLIAN
Emerging in August 2022, BianLian became known as a ransomware strain capable of swiftly encrypting files. The name BianLian draws inspiration from an ancient Chinese theatrical art form where performers, adorned in vibrant costumes and masks, would deftly change their masks' faces with a mere flick of a fan, almost in the blink of an eye.
Written in Golang and compiled as a 64-bit Windows executable, BianLian wreaked havoc across various sectors, including media and entertainment, manufacturing, and healthcare, during 2022 and 2023. On March 13, 2023, BianLian's extortion website listed 118 organizations as victims, with the majority (71%) hailing from the U.S.
At its peak, BianLian employed techniques to thwart analysis, such as triggering API calls capable of crashing sandboxes or automated analysis systems. Its objective was to encrypt all accessible drives on infected devices, and once the encryption process concluded, it erased itself. They made sure to encrypt systems, steal data, then threaten to publish the data. The ransomware met with considerable success until a team of researchers and analysts at Avast developed a decryptor for BianLian and made it publicly accessible. Now, the group has gone from being known as ransomware group that focuses on swift encryption, to both a ransomware and data extortion group.
BianLian switched to extortion-based data theft without encrypting systems in 2023. In May 2023, the Cybersecurity and Infrastructure Security Agency (CISA), in addition to government agencies in the U.S. and Australia, published a warning for organizations to remain vigilant regarding the threat actor and their new tactics.
In BianLian’s latest attack, the group targeted one of the world's oldest and largest charities, NGO Save the Children, stealing nearly 7TB of data including financial, human resources, personal, and medical information. Fortunately, the charity encountered no operational disruptions and maintained its usual functionality.
KARAKURT
In June 2022, CISA issued a warning concerning a ransomware group known as Karakurt. The threat actor, also recognized as Karakurt Team and Karakurt Lair, was labeled as "new" by most media outlets, but, in reality, Karakurt had been active since 2021.
Karakurt uses a range of tactics, techniques, and procedures that pose challenges for defense and mitigation efforts. Notably, they bypass the encryption step on compromised devices and files, opting instead to immediately extract data and withhold it until receiving their ransom payment. To date, the group has victimized organizations in both North America and Europe and has publicly disclosed several press releases or announcements to shame non-cooperating victims.
Karakurt generally targets organizations that have already experienced a security breach, acquiring data either through a third-party intrusion broker or stolen login credentials. Once in possession of this data, they threaten to release the data on the dark web. Non-compliant victims face public exposure as the group discloses sensitive information.
In December 2021, Karakurt claimed they stole data from 40 victims, spanning the period between September and November 2021. The identities of these victims remain undisclosed. Karakurt makes promises to erase the stolen data upon payment, however some victims have reported that the threat actors failed to honor this commitment.
Karakurt’s most recent victim was the McAlester Regional Health Center in Oklahoma. The group stole over 126GB of data, including 40 GB of DNA patient records. If negotiations were refused or if the health center did not pay the undisclosed demanded ransom, the group threatened to auction off the DNA patient records to the highest bidder on the dark web.
Stolen genetic material can be exploited for malicious intentions, such as blackmail or generating false paternity outcomes. Additionally, it can expose predispositions to diseases and preexisting medical conditions, which may impact employment opportunities, insurance costs, and even lead to societal discrimination, as highlighted in a DNA theft study published in Nature Reviews Genetics.
According to Cyber News, after breaching the organization, Karakurt responded with the following statements on their data leak site:
“Another medical center doesn't care about their patients' data,” Karakurt said about the hospital.
“126GB of this organization data includes medical information, personal documents, financial and accounting data and lots of HR documentation,” the group stated.
“40GB of DNA tests of patients is a bonus! Stay tuned,” it said.
Although Karakurt threatened to publish the stolen data by August 1, 2023, there is no confirmation that the group followed through on their threat.
CL0P
In June 2023, Cl0p exploited multiple MOVEit Transfer vulnerabilities, starting with CVE-2023-34362—an SQL injection vulnerability. This flaw allowed for escalated privileges and unauthorized access to victim systems. There were also several more MOVEit vulnerabilities discovered after the initial vulnerability. Despite prompt patches by Progress, Clop acted swiftly, compromising several companies in the following weeks.
The MOVEit Transfer vulnerabilities allowed Cl0p to steal data from U.S. banks, universities, hospitals, engineering firms, schools, and airlines. Once the data was stolen, Cl0p threatened to leak the data if ransom demands were not met. As a result of unmet demands, the sensitive information of millions of individuals was exposed on Cl0p’s data leak site.
Cl0P’s latest victim is the healthcare software company, Nuance Communications. Nuance uses Progress’s MOVEit software to transfer patient information. More than a dozen hospital systems, including UNC, DUKE, Atrium, and ECU, may have had personal data stolen by Cl0p.
reasons behind the switch
Based on Cisco Talos's incident response data, instances of data theft and extortion without any data encryption or ransomware usage increased by 25% from April 1 to the close of June 2023. These cases constituted 30% of the incidents to which the organization responded. Ransomware remained the second most frequently encountered threat, representing 17% of the engagements. Cl0p’s exploitation of the MOVEit vulnerabilities accounted for many of those extortion incidents, with BianLian on their heels.
There are several reasons why threat actors are starting to pivot from encryption to data extortion:
- Increased Profitability: Threat actors are shifting away from encryption towards data theft and extortion because it tends to be more financially rewarding. With data extortion, they can demand ransoms in exchange for not disclosing sensitive information, potentially earning more money than just offering decryption keys.
- Enhanced Leverage: Data theft and extortion give threat actors greater leverage over victims. They can threaten to expose confidential data, causing reputational damage, legal consequences, and regulatory fines, which compels victims to pay up.
- Reduced Technical Barriers: Implementing encryption and decryption mechanisms can be technically challenging. By focusing on data theft and extortion, threat actors can avoid the complexities of encryption while still causing significant harm and distress.
- Diverse Targets: Data theft and extortion can target a broader range of victims beyond those with valuable encrypted data. Threat actors can victimize organizations and individuals who may not be safeguarding their data with encryption, expanding their pool of potential targets and opportunities for profit.
- Easier Monetization: Data theft and extortion provide a more straightforward path to monetization compared to traditional encryption-based ransomware attacks. Threat actors can quickly convert stolen data into cash without the need for complex negotiation over decryption keys.
- Increased Fear and Compliance: The threat of data exposure is often more frightening to victims than encrypted data access denial. Threat actors exploit this fear to coerce victims into paying ransoms promptly, making data extortion a more psychologically effective tactic for ensuring compliance.
defense
In the realm of data extortion, maintaining backups remains crucial, but it won't provide sufficient protection against threat actors trying to compromise your organization's valuable data. An organization’s primary security focus should revolve around fortifying systems and networks against unauthorized access by threat actors.
It's essential to take an in-depth look data extortion groups like BianLian, Karakurt, and Cl0p, and understand why merely securing backups may not be the silver bullet needed to keep organizations safe. Of course, backups are still necessary, however, when confronting groups that threaten to leak sensitive, backups may offer limited reassurance.
Implementing an intrusion prevention system (IPS) is a cybersecurity best practice that will bolster your organization's overall security posture. An IPS is a network security tool designed to detect and thwart threats. It continually monitors the network for intrusion attempts and suspicious activities. When it identifies potential threats, it reports them to system administrators and employs various strategies to prevent attacks. These strategies may involve changing the security setup, halting the attack, or modifying the attack's content, all aimed at preventing successful attacks. Here are some actions the IPS takes when it detects a possible threat:
- Reprograms or reconfigures the firewall to stop a similar attack from happening in the future.
- Deletes malicious content or replaces malicious content that persists on networks after an attack.
- Terminates abused TCP sessions and blocks the offending source IP address or user account from accessing other network properties or target hosts.
Some of the benefits of implementing an IPS strategy include:
- Enhanced Security: IPS helps identify and block intrusion attempts, reducing the risk of successful attacks, data breaches, and unauthorized access to your network.
- Efficient Network Management: IPS can help optimize network performance by identifying and mitigating malicious traffic, ensuring resources are used efficiently.
- Real-time Threat Detection: It provides continuous monitoring, allowing for the immediate detection of threats as they occur, enabling rapid response.
How Avertium is Protecting Our Customers
- Avertium recommends utilizing our service for DFIR (Digital Forensics and Incident Response) to help you rapidly assess, contain, eradicate, and recover from a security incident like a malware attack.
- Expanding endpoints, cloud computing environments, and accelerated digital transformation have decimated the perimeter in an ever-expanding attack surface. Avertium offers Attack Surface Management, so you’ll have no more blind spots, weak links, or fire drills. See every threat in your attack surface, every device, every entry point, and every vulnerability. Our Attack Surface Management services include:
- Risk Assessments
- Pen Testing and Social Engineering
- Infrastructure Architecture and Integration
- Zero Trust Network Architecture
- Vulnerability Management
- Fusion MXDR is the first MDR offering that fuse together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is greater than the sum of its parts.
- Avertium offers Vulnerability Management (VM) to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
MITRE MAP(s)
8Base
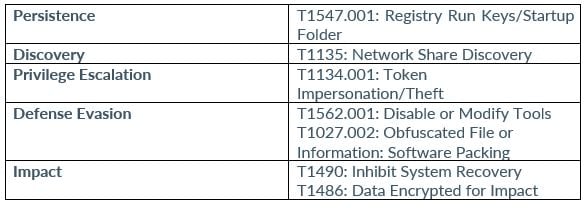
Karakurt
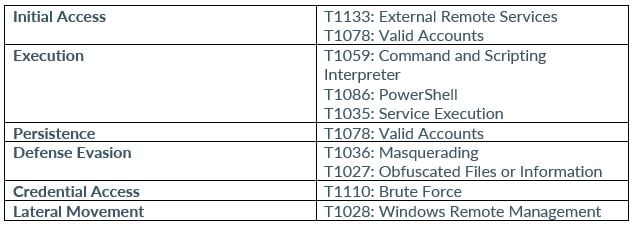
Cl0p
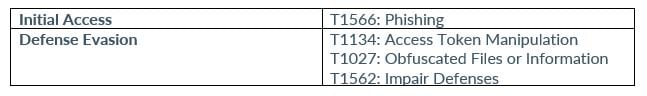
INDICATORS OF COMPROMISE (IOCs)
8Base
- SHA-256
- 518544e56e8ccee401ffa1b0a01a10ce23e49ec21ec441c6c7c3951b01c1b19c
- 5BA74A5693F4810A8EB9B9EEB1D69D943CF5BBC46F319A32802C23C7654194B0
- e142f4e8eb3fb4323fb377138f53db66e3e6ec9e82930f4b23dd91a5f7bd45d0
- 5d0f447f4ccc89d7d79c0565372195240cdfa25f
- C6BD5B8E14551EB899BBE4DECB6942581D28B2A42B159146BBC28316E6E14A64
- 518544E56E8CCEE401FFA1B0A01A10CE23E49EC21EC441C6C7C3951B01C1B19C
- AFDDEC37CDC1D196A1136E2252E925C0DCFE587963069D78775E0F174AE9CFE3
- MD5
- 20110FF550A2290C5992A5BB6BB44056
- 9769c181ecef69544bbb2f974b8c0e10
- URLs
- wlaexfpxrs[.]org
- admhexlogs25[.]xyz
- admlogs25[.]xyz
- admlog2[.]xyz
- dnm777[.]xyz
- serverlogs37[.]xyz
- dexblog[.]xyz
- blogstat355[.]xyz
- blogstatserv25[.]xyz
- File Name
- 3c1e.exe
- d6ff.exe
- 9f1a.exe
Karakurt
- Bitcoin Addresses
- bc1q25km8usscsra6w2falmtt7wxyga8tnwd5s870g
- bc1q3xgr4z53cdaeyn03luhen24xu556y5spvyspt8
- bc1q6s0k4l8q9wf3p9wrywf92czrxaf9uvscyqp0fu
- bc1q8ff3lrudpdkuvm3ehq6e27nczm393q9f4ydlgt
- bc1qa5v6amyey48dely2zq0g5c6se2keffvnjqm8ms
- bc1qenjstexazw07gugftfz76gh9r4zkhhvc9eeh47
- bc1qfp3ym02dx7m94td4rdaxy08cwyhdamefwqk9hp
- bc1qj7aksdmgrnvf4hwjcm5336wg8pcmpegvhzfmhw
- bc1qq427hlxpl7agmvffteflrnasxpu7wznjsu02nc
- bc1qq9ryhutrprmehapvksmefcr97z2sk3kdycpqtr
- bc1qqp73up3xff6jz267n7vm22kd4p952y0mhcd9c8
- bc1qrkcjtdjccpy8t4hcna0v9asyktwyg2fgdmc9al
- bc1qrtq27tn34pvxaxje4j33g3qzgte0hkwshtq7sq
- bc1qta70dm5clfcxp4deqycxjf8l3h4uymzg7g6hn5
- bc1qtm6gs5p4nr0y5vugc93wr0vqf2a0q3sjyxw03w
- bc1qw77uss7stz7y7kkzz7qz9gt7xk7tfet8k30xax
- bc1qx9eu6k3yhtve9n6jtnagza8l2509y7uudwe9f6
- bc1qxfqe0l04cy4qgjx55j4qkkm937yh8sutwhlp4c
- bc1qz9a0nyrqstqdlr64qu8jat03jx5smxfultwpm0
- MD5
- 074863c3352d6dda17dcb8bdc6a8929f
- 1bf171b1f388691c3985df6fb6c3f0d1
- 286aaf0974d06d9b02d11611b2acccef
- 3e9f31b4e2cd423c015d34d63047685e
- 8e6a8cfba63453bd545e0c78b3b3ed9c
- ca2883a7f300abd755706d3a9b55916b
- e2bce0f3162076fa56de5215fd31e3ab
- Other IoCs for Karakurt can be found here.
BianLian
- URL
- hxxp://zhgggga[.]in
- MD5
- 08e76dd242e64bb31aec09db8464b28f
- 0c756fc8f34e409650cd910b5e2a3f00
- 0cc30238204a3d3da6d588640e054af6
- 36171704cde087f839b10c2465d864e1
- ad5fbd52096e8bdc76d4052a5d8975a2
- b3cdf0489ff37fe65141be9363b9489c
- e245f8d129e8eadb00e165c569a14b71
- SHA1
- 3f3f62c33030cfd64dba2d4ecb1634a9042ba292
- 43921f6a8f07d9509590849bbe3f76f8f8d538e4
- 67f25f899228a52c6668a7663ff8cf3f9e4dff22
- 70d1d11e3b295ec6280ab33e7b129c17f40a6d2f
- 86447d6bcc862ebfa2366f751ce57de8b5948c9c
- cd8b84051d423f1b773a1b6804f0823618efdf3b
- e3baa1c3ee9aa1d5ae61187be2e20ea9cb57d538
- Other IoCs for BianLian can be found here.
Cl0p
- URL
- hxxp://tddshht.com/chkds[.]dll
- MD5
- 5da364a8efab6370a174736705645a52
- 6a2f114a8995dbeb91f766ac2390086e
- 775fb391db27e299af08933917a3acda
- 8a94163ddf956abd0ea92d89db0034e5
- d9d85bdb6a3ac60a8ba6776c661dbace
- e9115cc3280c16f9019e0054e059f4b8
- SHA1
- 77360abc473dc65c8bdd73b6459b9ea8fddb6f1d
- 77ad34334a370d85ca5e77436ed99f18b185eee3
- 792623e143ddd49c36f6868e948febb0c9e19cd3
- a9040ac0e9f482454e040e2a7d874ddc50e6f6ce
- d8bd44b7a8f136e29b31226f4edf566a4223266c
- edac3cf9533b6f7102f6324fadb437a0814cc680
- Other IoCs for Cl0p can be found here.
Supporting Documentation
Canadian dental service pays ransom in 8base ransomware attack - SiliconANGLE
FBI confirms BianLian ransomware switch to extortion only attacks (bleepingcomputer.com)
BianLian ransomware gang holds Save the Children hostage | Computer Weekly
Hackers threaten to auction off DNA patient records | Cybernews
Clop ransomware gang starts extorting MOVEit data-theft victims (bleepingcomputer.com)
Karakurt ransomware group targeting healthcare providers, HHS warns | SC Media (scmagazine.com)
Cyber criminals pivot away from ransomware encryption | Computer Weekly
Cyber attack: NC hospitals data breach by Russian cyber gang | Charlotte Observer
The Double Extortion Group, 8Base (avertium.com)
Cyberattack may have stolen data from N.C. hospitals (spectrumlocalnews.com)
CrowdStrike: More Cybercriminals Ditching Ransomware To Focus On Data Extortion | CRN
Ransomware gangs ditch encryption, embrace data extortion (axios.com)
BianLian Ransomware Pivots From Encryption to Pure Data-Theft Extortion (darkreading.com)
As Ransomware Gangs Shift To Data Extortion, Some Adopt A New Tactic: ‘Customer Service’ | CRN
An In-Depth Look at the Data Extortion Group, Karakurt (avertium.com)
Ransomware gangs move into pure extortion without encryption • The Register
BianLian ransomware gang holds Save the Children hostage | Computer Weekly
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.