An In-Depth Look at the Data Extortion Group, Karakurt
Executive Summary
This month, the Cybersecurity and Infrastructure Agency (CISA) issued a warning about a data extortion group called Karakurt. The threat actor is also known as Karakurt Team and Karakurt Lair, and although most media outlets are reporting the group as “new”, Karakurt has actually been active since 2021.
Karakurt has a variety of tactics, techniques, and procedures that make it difficult for defense and mitigation. They also skip the encryption process on compromised machines and files, and go straight for the extraction of data – holding the data until they receive their ransom payment. So far, the group has had victims in North America and Europe, and they have published several press releases or announcements shaming victims who haven’t cooperated. Let’s take a detailed look at Karakurt and why securing backups may not be enough to stop data extortion groups

karakurt - Data extortion
As we stated previously, even though Karakurt has been called a new data extortion group, the group has been active since June 2021. In September 2021, Accenture Security observed Karakurt intrusion clusters, as well as multiple sightings within a short timeframe. At that time, Karakurt impacted over 40 victims and was specifically targeting small companies or corporate subsidiaries as opposed to large corporations.
Additionally, Karakurt focuses on attacking organization’s that have already been compromised, obtaining data via a third-party intrusion broker or through stolen login credentials. After they obtain the data, they threaten to release it on their website that’s only accessible through the dark web. If victims don’t comply, they shame them publicly on the site by releasing sensitive data.
In December 2021, Karakurt claimed they had data from 40 victims between September and November of 2021. The names of the victims are not public. Karakurt promises to delete stolen data after payment is made but some victims reported that the threat actors didn’t keep their promise.
link to conti
Karakurt (which means black wolf in Turkish) is believed to be an arm of or in alliance with the ransomware group, Conti. If you recall, Avertium’s Cyber Threat Intelligence team mentioned Karakurt in a Threat Intelligence Report featuring Black Basta ransomware.
According to our partners, AdvIntel, Conti is currently rebranding as multiple ransomware groups and that the brand, not the organization, is shutting down. On May 19, 2022, Conti’s official website went offline, as well as their negotiations service site. Conti’s infrastructure (chat rooms, servers, proxy hosts, etc.) went through a massive reset.
The publicity function of Conti’s blog is still active, but the operational function of “Conti News” (used to upload new data to force victims to pay) is defunct – including infrastructure related to data uploads, negotiations, and the hosting of stolen data. AdvIntel believes that Conti can no longer support and obtain extortion and that the shutdown was not spontaneous but calculated. May 19, 2022 is Conti’s official date of death with their attack on Costa Rica being their final dance.
The attack on Costa Rica, which forced the country to declare a state of emergency, was Conti’s way of keeping the illusion that they were still active and diverting everyone’s attention, while working on their restructuring. During the diversion tactics, Conti’s extension groups such as Karakurt were actively and silently attacking organizations.
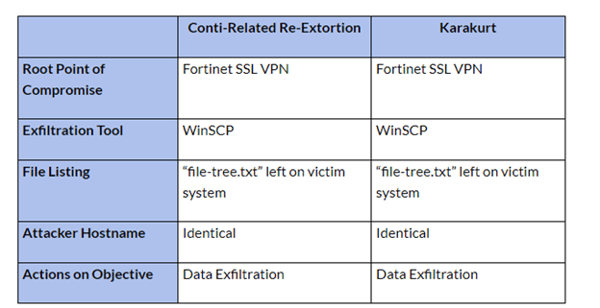
Researchers observed that there was some overlap between some of Karakurt’s attacks and Conti’s attacks. The two groups use some of the same tools for exfiltration and leave behind a file listing of exfiltrated data (file-tree.txt) in their victim’s environment. When remotely accessing victims’ networks, both groups use the same attacker host name.
Image 1: Conti Compared to Karakurt
Source: ArcticWolf.com
n addition to using some of the same tools, Karakurt was observed sending large sums of cryptocurrency to Conti wallets. Chainanalysis, a blockchain analysis team, observed Karakurt moving 11.6 Bitcoin ($472,000) into a Conti wallet. They also observed several Karakurt victim payment addresses hosted by wallets that house Conti victim payment addresses.
tactics and techniques
Karakurt’s initial access method is primarily via internet-facing systems on virtual private networks (VPN) using legitimate credentials. There isn’t enough forensic evidence to determine how they obtain the credentials, but one possibility is through the exploitation of vulnerable VPN devices. All observed cases of those devices included inconsistent or absent use of multi-factor authentication for user accounts.
According to Accenture Security, Karakurt uses credentials, service creation, remote management software, and distribution of C2 beacons via Cobalt Strike to further their foothold and maintain persistence. Recently, the threat actors didn’t deploy backup persistence by using Cobalt, but instead used the VPN IP pool or AnyDesk to allow external remote access to compromised devices.
To move laterally in a system, Karakurt leverages previously obtained user, service, and administrator credentials. They also leverage Mimikatz in at least one intrusion set, and leverage PowerShell to dump ntds.dit and exfiltrate it. Karakurt uses these techniques and tools to escalate privileges on an as needed basis.
Karakurt evades defenses by using pre-existing tools and techniques, as well as remote management software. Accenture Security noted that Karakurt avoids using common post-exploitation tools or commodity malware in favor of credential access. The approach allows the threat actor to evade detection and bypass security tools, such as EDR solutions.
If the previously mentioned tools aren’t already on their victims’ networks, the group downloads common remote management and file transfer utilities to support later exfiltration (AnyDesk, 7zip, etc.). WinZip and 7zip are using for compression, while Rclone or FileZilla (SFTP) is used for staging and final exfiltration to Mega.io cloud storage.
Why Backups Aren't Enough
When it comes to data extortion, backups are still important, but they won’t be enough to keep your organization from losing valuable data to Karakurt. As we stated before, Karakurt is bypassing file encryption and is focusing on data exfiltration instead. This means that your security focus should be based on keeping threat actors out of your systems and networks.
Of course, backups are necessary and there will never be a time when they are not needed, but when a data extortion group like Karakurt blackmails your organization by threatening to leak sensitive data, backups mean little to nothing. Focusing on keeping intruders out of your cyber environment in the first place will give you more leverage over data extortion groups. Implementing an intrusion prevention system (IPS) is a cyber security best practice that will help keep your organization safe.
What is an IPS?
An IPS is an intrusion prevention system that offers protection for networks by detecting and preventing threats. The system constantly monitors the network for intrusion prevention mechanisms and also checks for potential malicious events. Once incidents are found, the IPS reports those incidents to system administrators and takes measures to prevent possible attacks. How does an IPS prevent attacks from succeeding? The IPS prevents attacks by using different response strategies including altering the security environment, stopping an attack itself, or altering the content of an attack.
The IPS operates by scanning traffic on a network, avoiding different risks such as:
- Risk of viruses
- Risk of worms
- Risk of DDoS (Distributed Denial of Service) assault
- Risk of assault by DoS (Denial of Service)
- Risk of diverse types of vulnerabilities
Also, the IPS inspects any packet that passes through a network via real-time packet inspection. If a potential threat is observed, the IPS does one of the following:
- Reprograms or reconfigures the firewall to stop a similar attack from happening in the future.
- Deletes malicious content or replaces malicious content that persists on networks after an attack.
- Terminates abused TCP sessions and blocks the offending source IP address or user account from accessing other network properties or target hosts.
If your organization implements an IPS strategy, there will be several benefits, including:
- Your organization will reduce the risk of security incidents.
- An IPS provides complex security for threats.
- An IPS will notify system administrators immediately when suspicious behavior is observed.
- An IPS reduces network maintenance for IT personnel
- An IPS prevents threats, like DoS attacks, DDoS attacks, zero-day attacks, and brute-force attacks.
Is Data Extortion a New Trend?
Karakurt is the second data extortion group Avertium has covered in a short span of time. The first data extortion group that made headlines was Lapsus$. Avertium became aware of the data extortion gang Lapsus$ after they breached authentication company, Okta Inc. However, Okta Inc. was not the only organization that became a victim of Lapsus$. In March 2022, Lapsus$ breached Globant and then breached T-Mobile in April 2022, stealing the company’s source code. Lapsus$ also breached Microsoft, Samsung, Ubisoft, and Nvidia.
Like Karakurt, Lapsus$ focused heavily on data extortion, gaining initial access to networks by compromising personal or private accounts. This gave them access to look for additional credentials – ultimately giving them access to corporate systems. After gaining access to their targeted network, Lapsus$ exploits unpatched vulnerabilities on internally accessible servers. The threat actors also finds exposed credentials by searching code repositories and collaboration platforms.
Once Lapsus$ obtains the information they need, they threated to leak the information if they aren’t paid a ransom. Lapsus$ has made an estimated $14 million in Bitcoin. As you can see, data extortion is not a new idea, but it may become a new trend amongst threat actors. Cutting out file encryption and holding data ransom has more of an impact when trying to extort organizations. Threat actors know that most would be willing to pay if there is a risk of sensitive data being leaked, making backups useless.
How Avertium is Protecting Our CUSTOMERS
Even with anti-malware solutions installed, Karakurt is a great risk to organizations. Karakurt can go undetected by EDR, making organizations everywhere vulnerable to an attack. However, Avertium has advanced services that can help keep your organization safe:
- Avertium recommends utilizing our service for DFIR (Digital Forensics and Incident Response) to help you rapidly assess, contain, eradicate, and recover from a security incident like a malware attack.
- MDR provides an in-depth investigation into potential threats on an organization’s network. Avertium’s risk-based approach to managed security delivers the right combination of technology, field-validated threat intelligence, and resource empowerment to reduce complexity, streamline operations, and enhance cybersecurity resilience. If you need a more advanced security solution, MDR is the next step. MDR is an outsourced security control solution that includes the elements of EDR, enhanced with a range of fundamental security processes.
- Avertium offers security consulting services to develop robust internal security policies.
- Expanding endpoints, cloud computing environments, and accelerated digital transformation have decimated the perimeter in an ever-expanding attack surface. Avertium offers Attack Surface Management, so you’ll have no more blind spots, weak links, or fire drills.
- Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
- Implement XDR as a prevention method. Our XDR is a combination of monitoring software like LogRhythm, Microsoft Azure Sentinel, or AlienVault, combined with endpoint protection such as SentinelOne. XDR platforms enable cybersecurity through a technology focus by collecting, correlating, and analyzing event data from any source on the network. This includes endpoints, applications, network devices, and user interactions.
- Avertium offers user awareness training through KnowBe4. The service also includes Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
- Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
Avertium’s Recommendations
- Implement MFA where possible to authenticate corporate accounts, with admin accounts being cross platformed and MFA enforced.
- Have a robust crisis management and incidence response plan in place.
- All internet-facing security and remote access appliances should be updated.
- Don’t store unprotected credentials in files and scripts on shared locations.
- Using EDR across your cyber environment is a must (target at least 90% coverage of endpoints and workload visibility).
- Admin accounts should only be used for administrative purposes and should never be connected to the network or to browse the internet.
- Implement cyber security best practices against malware, such as patching, updating anti-virus software, whitelisting where feasible, and maintaining strict network egress policies.
- Disable RDP on external-facing devices.
- Maintain a robust and routine user-awareness training regimen for users of all systems.
- Threat actors exploit older systems with existing vulnerabilities. Organizations should patch infrastructure to the highest available level.
- Having a strong corporate password policy (that includes industry standards for password length and complexity) will help keep your organization safe.
- When hunting for threat actor TTPs, include common “living off the land” techniques to proactively detect and respond to a cyber attack.
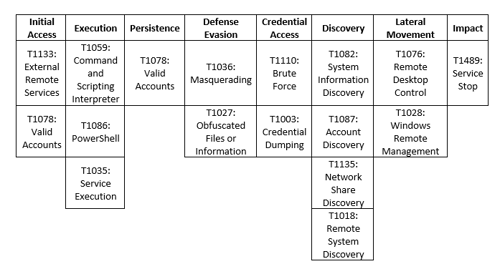
MITRE Map
Indicators of Compromise (IoCs)
- Mark[.]hubert1986[@]gmail[.]com
- Karakurtlair[@]gmail[.]com
- Personal[.]information[.]reveal[@]gmail[.]com
- ripidelfun1986[@]protonmail[.]com
- armada[.]mitchell94[@]protonmail[.]com
- gapreappballye1979[@]protonmail[.]com
- confedicial[.]datas[.]download[@]protonmail[.]com
- hxxps://omx5iqrdbsoitf3q4xexrqw5r5tfw7vp3vl3li3lfo7saabxazshnead[.]onion
- Rclone[.]exe
- AnyDesk[.]exe
- 3e625e20d7f00b6d5121bb0a71cfa61f92d658bcd61af2cf5397e0ae28f4ba56
- Msuxxx[.]dll
- c33129a680e907e5f49bcbab4227c0b02e191770
- 030394b7a2642fe962a7705dcc832d2c08d006f5
- 0E50B289C99A35F4AD884B6A3FFB76DE4B6EBC14
- 3[.]bat
- C[.]bat
- Filter[.]txt
- Rclone[.]conf
- Dllhosts[.]exe
- Msxsl[.]exe
- 8B516E7BE14172E49085C4234C9A53C6EB490A45
- fdb92fac37232790839163a3cae5f37372db7235
- 7E654C02E75EC78E8307DBDF95E15529AAAB5DFF
- 4D7F4BB3A23EAB33A3A28473292D44C5965DDC95
- 10326C2B20D278080AA0CA563FC3E454A85BB32F
- 86366bb7646dcd1a02700ed4be4272cbff5887af
- 563BC09180FD4BB601380659E922C3F7198306E0CAEBE99CD1D88CD2C3FD5C1B
- 5E2B2EBF3D57EE58CADA875B8FBCE536EDCBBF59ACC439081635C88789C67ACA
- 712733C12EA3B6B7A1BCC032CC02FD7EC9160F5129D9034BF9248B27EC057BD2
- bc1qfp3ym02dx7m94td4rdaxy08cwyhdamefwqk9hp
- bc1qw77uss7stz7y7kkzz7qz9gt7xk7tfet8k30xax
- bc1q8ff3lrudpdkuvm3ehq6e27nczm393q9f4ydlgt
- bc1qenjstexazw07gugftfz76gh9r4zkhhvc9eeh47
- bc1qxfqe0l04cy4qgjx55j4qkkm937yh8sutwhlp4c
- bc1qrtq27tn34pvxaxje4j33g3qzgte0hkwshtq7sq
- bc1q25km8usscsra6w2falmtt7wxyga8tnwd5s870g
- bc1qta70dm5clfcxp4deqycxjf8l3h4uymzg7g6hn5
- bc1qrkcjtdjccpy8t4hcna0v9asyktwyg2fgdmc9al
- bc1q3xgr4z53cdaeyn03luhen24xu556y5spvyspt8
- bc1q6s0k4l8q9wf3p9wrywf92czrxaf9uvscyqp0fu
- bc1qj7aksdmgrnvf4hwjcm5336wg8pcmpegvhzfmhw
- bc1qq427hlxpl7agmvffteflrnasxpu7wznjsu02nc
- bc1qz9a0nyrqstqdlr64qu8jat03jx5smxfultwpm0
- bc1qq9ryhutrprmehapvksmefcr97z2sk3kdycpqtr
- bc1qa5v6amyey48dely2zq0g5c6se2keffvnjqm8ms
- bc1qx9eu6k3yhtve9n6jtnagza8l2509y7uudwe9f6
- bc1qtm6gs5p4nr0y5vugc93wr0vqf2a0q3sjyxw03w
- bc1qqp73up3xff6jz267n7vm22kd4p952y0mhcd9c8
SUPPORTING DOCUMENTATION
An In-Depth Look at Black Basta Ransomware (avertium.com)
Karakurt Rises from Its Lair | Accenture
Why backups aren’t enough in the fight against ransomware | Kaspersky official blog
A Guide To Intrusion Prevention System In 6 Simple Points (jigsawacademy.com)
An In-Depth Look at Data Extortion Group, Lapsus$ (avertium.com)
Feds warn consumers against paying Karakurt hacker ransoms - Top Class Actions
Karakurt Extortion Group Connected to Conti Ransomware? (secureworld.io)
Karakurt Team hits North America and Europe with data theft and extortion (techrepublic.com)
Karakurt Data Extortion Group | CISA
CISA Warns of Karakurt Extortion Group | Decipher (duo.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.
Related Resource: An In-Depth Look at Black Basta Ransomware