Super Bowl Weekend: BlackByte & Coinbase Were the Real Stars of the Show
Every year millions of people tune in to watch one of the most anticipated sporting events of the year – the NFL Super Bowl. This year, an estimated 101.1 million people watched as the Los Angeles Rams defeated the Cincinnati Bengals by three points. However, while most of America was being entertained by football, Dr. Dre, and Mary J. Blige, two cyber security incidents took place that flew under the radar.
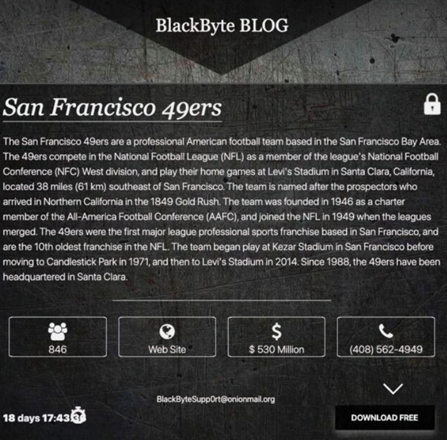
By now, you’ve probably heard about the San Francisco 49ers website being compromised by BlackByte ransomware. The ransomware group compromised the site on the same day that the attention of millions was focused on a major sporting event. According to ARS Technica, a 379 MB file (containing billing statements sent by the team to its partners - AT&T and Pepsi) was stolen and held for ransom. This contributes to the theory that threat actors take advantage of significant events and dates.
In addition to the San Francisco 49er breach, the cryptocurrency company Coinbase made headlines when their Super Bowl commercial featured a QR code randomly bouncing on TV screens for 60 seconds. The code was meant to be scanned by viewers, who would then be directed to click on a link for the company’s website. What many are describing as marketing genius, cyber security analysts are saying this kind of advertisement opens the door for threat actors to take advantage of naïve people.
Let’s take a look at two significant security incidents that happened during Super Bowl Weekend and why significant dates and events create perfect opportunities for threat actors.
blackbyte and the san francisco 49ers
BlackByte ransomware is a ransomware-as-a-service (RaaS) group that first surfaced in July 2021. The group encrypts the files of physical and virtual servers on compromised Windows host systems. After encrypting, BlackByte leaves a ransom note in all the directories where the encryption took place. The note includes a [.onion] website where victims can find instructions for paying a ransom in exchange for a decryption key. The ransomware gang is known for using known Microsoft Exchange Server vulnerabilities (ProxyShell - CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207) to gain access to their victims’ network. After gaining access, BlackByte deploys tools ad moves laterally across the network before escalating privileges so they can exfiltrate and encrypt files.
On February 11, 2022, the FBI and the U.S. Secret Service issued a warning stating that as of November 2021, BlackByte ransomware attacked multiple U.S. and foreign businesses, including at least three critical infrastructure entities within the U.S (government facilities, financial, and food & agriculture). Two days later, on Super Bowl Sunday, BlackByte successfully compromised the network of the San Francisco 49ers and stole a 379 MB file containing billing statements for Pepsi and AT&T – leaving the 49ers organization surprised.
According to Threat Post, the NFL organization described the breach as a “network security incident that resulted in temporary disruption to certain systems on their corporate IT network.” The breach was confirmed by the NFL organization on Monday and the 49ers brought in a third-party team to assist with the security breach. The Chief Security Scientist and Advisory CISO at Privileged Access Management (PAM), Joseph Carson, stated that the attack was more than likely executed by an affiliate due to BlackByte being a RaaS operation.
Image 1: BlackByte's Blog
When the NFL franchise confirmed the attack via an emailed statement, BlackByte followed up and posted a message on their dark web site in an attempt to shame the 49ers and force them into giving them a large ransom in exchange for a decryption key and the promise that the ransomware gang wouldn’t leak the organization’s data.
Source: Arstechnica.com
According to the FBI, there are some cases where BlackByte only has partially encrypted files. For those cases where decryption isn’t possible, some data recovery can occur. With previous versions of BlackByte, a .png file from two IP addresses were downloaded prior to encryption - 185.93.6.31 and 45.9.148.114.
 Image 2: Bleeping Computer Forum Post
Image 2: Bleeping Computer Forum Post
BlackByte was initially discovered in July 2021 after members discussed the threat actor in a Bleeping Computer forum.
Fortunately for victims, an early version of BlackByte’s ransomware contained a flaw which exposed encryption keys the group used to lock their victim’s data. In October 2021, the bug allowed security firm Trustwave to release a decryptor tool that recovered data for free.
Source: BleepingComputer
According to Trustwave, BlackByte’s ransomware is interesting and odd due to the following:
- “Same as other notorious ransomware variants like REvil, BlackByte also avoids systems with Russian and ex-USSR languages.
- It has a worm functionality similar to RYUK ransomware.
- It creates a wake-on-LAN magic packet and sends it to the target host - making sure they are alive when infecting them.
- The author hosted the encryption key in a remote HTTP server and in a hidden file with .PNG extension.
- The author lets the program crash if it fails to download the encryption key.
- The RSA public key embedded in the body is only used once, to encrypt the raw key to display in the ransom note – that’s it.
- The ransomware uses only one symmetric key to encrypt the files.” – Trustwave.com
Additionally, ransom note contains a link to an auction site. However, the auction site makes a claim that doesn’t add up. The site states that it exfiltrates data from its victims, yet the ransomware doesn’t have exfiltration functionality. Trustwave believes the claim was designed to scare victims into paying the ransom. BlackByte’s ransomware also uses the same raw key to encrypt files and a symmetric-key algorithm (AES).
Critical Infrastructure
In addition to breaching the San Francisco 49ers, BlackByte has also been responsible for attacking critical infrastructure. Earlier, we mentioned that the FBI issued a warning regarding BlackByte ransomware just days before the threat actor attacked the 49ers. The three areas of U.S. critical infrastructure include: government facilities, financial, and food & agriculture).
According to Erick Kron, a security awareness advocate at KnowBe4, BlackByte knows that attacking the systems of critical infrastructure will increase the chances of victims paying the ransom. However, attacking the sector also draws attention from law enforcement, but given the modest rate at which threat actors are taken down, most cyber criminals are willing to take that risk.
Limited budgets, aging equipment, and understaffing may be responsible for making critical infrastructure and government particularly vulnerable to ransomware attacks. While those sectors may have become more vulnerable over the years, there is still something that can be done. Most threat actors focus on two attack vectors: email phishing and remote access portal attacks. If you train users on how to spot and report phishing emails, along with monitoring remote access portals for brute force attacks, then the threats can be countered.
Conti
According to our partners, AdvIntel, Conti may actually be behind the 49ers breach. AdvIntel intercepted a Cobalt Strike IoC used in the breach – an IoC that has been deployed by Conti in past attacks. This would explain how a smaller, lesser-known organized ransomware gang was able to orchestrate a major data theft.
AdvIntel also stated that Conti has been targeting the 49ers since December 14, 2021. They know this because their breach pulse reported a direct network security breach (via Cobalt Strike) for the San Francisco 49ers football team. Cobalt Strike beacon was used by BlackByte to move laterally and silently through the network in order to investigate it and map it to full capacity, rather than hit it directly.
“With the use of Cobalt Strike, the Conti team who began the operation against 49ers on December 14, 2021, were able to compromise the victim’s primary domain, and get access to the local shares and core network segments for several departments, including the team’s finance and accounting sectors. Conti’s tactics in the past have been to escalate their initial access further into the domain computers, controllers, guests, and users. Using its unique adversarial insight, AdvIntel was not only able to spot the initial compromise by finding the Cobalt Strike intrusion, but also identified the actor behind the attack (the likely Patient Zero), as well as the scale of initial intrusion.” – AdvIntel
AdvIntel is confident that BlackByte was working under Conti in the San Francisco 49ers breach, given BlackByte’ s lesser-known presence and internal structure when compared to Conti’s.
coinbase and qr code safety
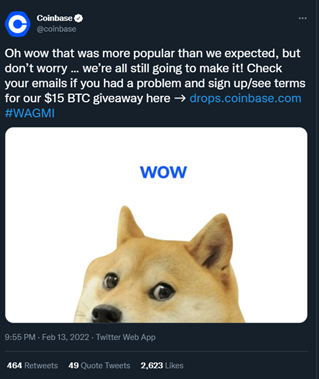
Super Bowl Sunday is often considered the Super Bowl of marketing for advertisers as well. Every brand you can think of tries their best to grab advertisement time if they have the capital to do so. On February 13, 2022, a QR code bounced randomly on the television screens of millions of people during a commercial – reminiscent of an early 2000s screen saver. Initially, people didn’t know what to make of the QR code but when they realized it was meant to be scanned, they scanned it.
After scanning the code, people were directed to click on a Coinbase website link. The link was supposed to direct them to a $3 million giveaway, but instead of everyone getting their share of the $3 million pie, the Coinbase website crashed due to too much traffic flooding their servers. Cryptocurrency and NFTs seem to be a popular topic of discussion as of late. Even Norton 360 and Avira jumped on the trend when they decided to offer their customers a built-in cryptominer so they can mine for cryptocurrency. But what happens when a cryptocurrency company like, Coinbase, advertises their cryptocurrency via an innocuous QR code advertisement during a Super Bowl Sunday commercial break? An unintentional DDoS attack happens.
Image 3: Coinbase Tweet
Source: Twitter
Unintentional DDoS attacks, also known as the “hug-of-death”, happen when a website distributes their link on a platform with the hopes that it will drive traffic to their site. Under normal circumstances, this seems like great advertising. However, when millions of people are watching an ad, that means a lot of those people will click on a link even if only curious. In Coinbase’s case, their ad was wildly successful, and their website crashed as a result. They simply didn’t have the bandwidth to withstand such a large amount of traffic (20 million people), therefore, their servers crashed and made their website inaccessible.
To prevent the “hug of death”, organizations should architect their application for scale by using patterns like: HTTP caching headers, auto-scaling groups, edge-caching with CDNs, and other methods that ensure your site can withstand a large burst of traffic.
QR Code Safety
About a month prior to Super Bowl Sunday, the FBI issued a report warning about the dangers of scanning anonymous QR codes. Since the COVID-19 pandemic, QR codes have become a popular way to do business. We scan them for access to restaurant menus, documents, and even to conduct financial business. With any convenient, yet popular technology vehicle, there will be a fair number of exploits.
The FBI’s warning pertained to threat actors taking advantage of QR codes by tampering with them and redirecting victims to malicious websites. The websites attempt to steal confidential data like banking information or identifiable information.
“Malicious QR codes may also contain embedded malware, allowing a criminal to gain access to the victim's mobile device and steal the victim's location as well as personal and financial information. The cybercriminal can leverage the stolen financial information to withdraw funds from victim accounts.” – FBI
The QR code for Coinbase is a good example of how people scan codes that they aren’t sure about.
Image 4: QR Code Scam on Parking Meters
While we know that the QR code in the ad was definitely for Coinbase and not malicious, how do we know that a large ransomware group with a lot of capital (BlackMatter, Conti, etc.) won’t buy advertising space and place another unidentifiable QR code for millions of people to scan?
Source: Twitter
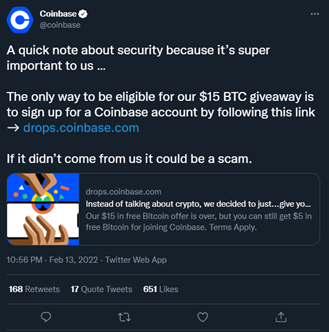
QR codes are not inherently malicious, so the security around them shouldn’t be overblown. However, it’s still important to exercise caution when scanning QR codes to be sure you aren’t being redirected to a phishing website. For example, your phone may show you the website you are being directed to after you scan the QR code. You should always exercise caution when clicking on a website by doing your due diligence and researching any link that has the potential to compromise our device.
Image 5: Coinbase Tweet About Potential Scams
Source: Twitter
attackers that use signifiant dates and events to their advantage
A lot of times threat actors will use significant dates and events to attack certain countries because they know that almost everyone is focused on the main attraction. In this report, the main attraction was Super Bowl Sunday. The attacks on Kaseya and Colonial Pipeline also happened around dates when the U.S. was celebrating - Fourth of July weekend and Mother’s Day weekend.
In the attack on Kaseya, Fourth of July weekend allowed REvil to deploy a massive supply-chain cyber attack. The attack impacted 1,000 businesses in 17 countries and led to a shutdown of Kaseya’s VSA servers. Researchers reported that REvil intentionally waited until the Fourth of July weekend to strike.
Colonial Pipeline was attacked on Mother’s Day weekend by DarkSide. The RaaS gang deployed ransomware that took down the largest fuel pipeline in the U.S., resulting in a week-long suspension of operations across the East Coast. There was also speculation from cyber security researchers regarding the timeliness of the attacks – Mother’s Day weekend.
During major holidays and events like Super Bowl Sunday, threat actors know that most organizations operate on a skeleton crew. They also know that organizations will be less alert during those times because they may be distracted by the festivities surrounding the event or they simply don’t have the bandwidth to monitor as diligently as they generally would.
Major U.S. holidays mean that there’s less staff keeping an eye out for threats, which means more opportunities for attackers to make their move. If employees are out of town or enjoying time off with family, it’s more difficult to react and to react quickly to an attack making its way through a company’s network. This extra time gives threat actors leverage and the chance to try various passwords and usernames, as well as extend their reach to more devices.
During these vulnerable moments, companies have been known to call a third-party to deal with an attack. If you recall, the San Francisco 49ers hired a third-party to help them mitigate the attack executed by BlackByte. Companies are also known to pay a large ransom before the holiday weekend or season ends. Protecting your company and employing monitoring tools while employees are scarce is imperative.
How Avertium is Protecting Our CUSTOMERS
Avertium offers the following service to help protect your organization from ransomware attacks:
- Avertium recommends utilizing our service for DFIR (Digital Forensics and Incident Response) to help you rapidly assess, contain, eradicate, and recover from a security incident like a malware attack.
- Avertium offers vulnerability management as a service (VMaaS) to remove any unnecessary applications.
- Implement XDR as a prevention method. Our XDR is a combination of monitoring software like LogRhythm, Microsoft Azure Sentinel, or AlienVault, combined with endpoint protection such as SentinelOne. XDR platforms enable cybersecurity through a technology focus by collecting, correlating, and analyzing event data from any source on the network. This includes endpoints, applications, network devices, and user interactions.
- You should also include a Zero Trust Architecture, like AppGate, to stop malware lateral movement.
Avertium offers the following services to help protect your organization from a phishing attack:
- KnowBe4 also offers a Holiday Cybersecurity Resource Kit to help equip end users with information and educate them on social engineering attacks. They also offer a free phishing security test to see if uses fall for convincing phishing attacks.
Avertium’s Recommendations
Tips for ransomware:
- Backups – please ensure your organization has secure offsite backups.
- Run up-to-date security solutions to ensure your organization’s computers are protected with the latest security patches against ransomware like BlackByte.
- Encrypt sensitive data wherever possible.
- Educate your staff about the various ways cybercriminals launch attacks and steal data.
- Practice good cyber hygiene
- Ensure antivirus and antimalware software signatures are up to date.
- Implement application allow listing.
- Ensure user privileged accounts are limited.
- Employ MFA.
- Implement cybersecurity best practices.
Tips for Conti from Avertium and our partner, AdvIntel:
- Monitoring for network segmentation, network hierarchy, and abnormal in-network behaviors, taking action as needed. Both Bazar and Conti will focus on extensive lateral movement, privilege escalation, and obtaining domain accesses with the subsequent use of compromised domain admins.
- Change of passwords and monitoring of any directories containing said passwords, as well as monitoring of domain admins and active directory.
- Advanced monitoring for any signs of CS beacons / CS sessions opened, Metasploit usage, Kerberoasting, and/or any PowerShell commands, since all these tools are ubiquitous for Conti attacks.
- Conti will sometimes use corporate VPN compromise and TrickBot delivery as an alternative means for attack initiation. Tracking externally exposed endpoints is therefore critical.
- Tracking IP-related & host-related indicators. As with any infectious botnet, Bazar is communicating with C2 from their bots. This may enable tracking of abnormal signaling and identifying the infection.
- Rclone and other data exfiltration command-line interface activities can be captured through proper logging of process execution with command-line arguments.
- Special security protocol, password updates, and account security measures for Veeam should be implemented to prevent Veeam account takeover. Enabled backups tremendously decrease Conti’s ransom demands and can likely lead to data recovery with zero payments to the Conti collective.
Tips for phishing, as well as dates and events:
- Don’t click on random links
- Check the web address
- Don’t hand over your credentials for sensitive information (bank account, healthcare logins, etc.)
- Run phishing campaign simulation tests regularly.
- Keep a clean machine. Be sure that all internet-connected devices ‒ including PCs, smartphones, and tablets ‒ are free from malware and infections by running only the most current versions of software, web browsers and other apps.
- Use secure Wi-Fi.
- Lock down your login. Create long and unique passphrases for all accounts and use multi-factor authentication wherever possible.
MITRE TTPS
BlackByte Ransomware (Conti)
- [T1027] Obfuscated Files for Information
- [T1057] Process Discovery
- [T1518] Software Discovery
- [T1486] Data Encrypted for Impact
- [T1592] Gather Victim Host Information
- [T1133] External Remote Services
- [T1106] Native API
- [T1083] File and Directory Discovery
- [T1140] Deobfuscate/Decode Files or Information
- [T1489] Service stop
- [T1490] Inhibit System Recovery
Phishing
- [T1566] Phishing
- [001] Spearphishing Service
- [002] Phishing: Spearphishing Link
- [T1212] Exploitation for Credential Access
Indicators of Compromise (IoCs)
BlackByte
|
0c7b8da133799dd72d0dbe3ea012031e |
|
11e35160fc4efabd0a3bd7a7c6afc91b |
|
1473c91e9c0588f92928bed0ebf5e0f4 |
|
1785f4058c78ae3dd030808212ae3b04 |
|
28b791746c97c0c04dcbfe0954e7173b |
|
296c51eb03e70808304b5f0e050f4f94 |
|
31f818372fa07d1fd158c91510b6a077 |
|
405cb8b1e55bb2a50f2ef3e7c2b28496 |
|
4ce0bdd2d4303bf77611b8b34c7d2883 |
|
4d2da36174633565f3dd5ed6dc5033c4 |
|
51f2cf541f004d3c1fa8b0f94c89914a |
|
52b8ae74406e2f52fd81c8458647acd8 |
|
58e8043876f2f302fbc98d00c270778b |
|
5c0a549ae45d9abe54ab662e53c484e2 |
|
5f40e1859053b70df9c0753d327f2cee |
|
659b77f88288b4874b5abe41ed36380d |
|
695e343b81a7b0208cbae33e11f7044c |
|
7139415fecd716bec6d38d2004176f5d |
|
8320d9ec2eab7f5ff49186b2e630a15f |
|
8dfa48e56fc3a6a2272771e708cdb4d2 |
|
9344afc63753cd5e2ee0ff9aed43dc56 |
|
959a7df5c465fcd963a641d87c18a565 |
|
a77899602387665cddb6a0f021184a2b |
|
a9cf6dce244ad9afd8ca92820b9c11b9 |
|
ad29212716d0b074d976ad7e33b8f35f |
|
ae6fbc60ba9c0f3a0fef72aeffcd3dc7 |
|
b8e24e6436f6bed17757d011780e87b9 |
|
c010d1326689b95a3d8106f75003427c |
|
c13bf39e2f8bf49c9754de7fb1396a33 |
|
cd7034692d8f29f9146deb3641de7986 |
|
cea6be26d81a8ff3db0d9da666cd0f8f |
|
d2a15e76a4bfa7eb007a07fc8738edfb |
|
d4aa276a7fbe8dcd858174eeacbb26ce |
|
d63a7756bfdcd2be6c755bf288a92c8b |
|
d9e94f076d175ace80f211ea298fa46e |
|
df7befc8cdc3c5434ef27cc669fb1e4b |
|
e2eb5b57a8765856be897b4f6dadca18 |
|
e46bfbdf1031ea5a383040d0aa598d45 |
|
eed7357ab8d2fe31ea3dbcf3f9b7ec74 |
|
eef977108c7a7aef512532cc6e2f49cc |
|
7273bf0db30a12428f7046ef99ebe3e7472cdfbe |
|
c90f32fd0fd4eefe752b7b3f7ebfbc7bd9092b16 |
|
ee1fa399ace734c33b77c62b6fb010219580448f |
|
1df11bc19aa52b623bdf15380e3fded56d8eb6fb7b53a2240779864b1a6474ad |
|
884e96a75dc568075e845ccac2d4b4ccec68017e6ef258c7c03da8c88a597534 |
|
91f8592c7e8a3091273f0ccbfe34b2586c5998f7de63130050cb8ed36b4eec3e |
|
92ffb5921e969a03981f2b6991fc85fe45e07089776a810b7dd7504ca61939a3 |
|
9bff421325bed6f1989d048edb4c9b1450f71d4cb519afc5c2c90af8517f56f3 |
|
d3efaf6dbfd8b583babed67046faed28c6132eafe303173b4ae586a2ca7b1e90 |
|
f8efe348ee2df7262ff855fb3984884b3f53e9a39a8662a6b5e843480a27bd93 |
|
185.93.6[.31] |
|
45.9.148[.114] |
Supporting Documentation
FBI and U.S. Secret Service Warning – BlackByte Ransomware
Stay Vigilant With Cybersecurity During the Holidays (avertium.com)
BlackByte Tackles the SF 49ers & US Critical Infrastructure | Threatpost
Hacking group is on a tear, hitting US critical infrastructure and SF 49ers | Ars Technica
BlackByte Ransomware – Pt. 1 In-depth Analysis | Trustwave
ProxyShell exploitation leads to BlackByte ransomware - Red Canary
Coinbase Super Bowl marketing stunt prompts debate over QR code security | IT PRO
Coinbase's Mystery QR Code Super Bowl Ad Is a Security Nightmare | PCMag
Introducing Norton 360 and Avira's Built-In Cryptocurrency Miners (avertium.com)
Stay Vigilant With Cybersecurity During the Holidays (avertium.com)
The Reddit Hug-of-Death & Other Causes of Website Crashes (wpengine.com)
Types of Denial-of-Service Attacks - DOS Mitigation Strategies | Okta Developer
Internet Crime Complaint Center (IC3) | Cybercriminals Tampering with QR Codes to Steal Victim Funds
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.
 DOWNLOAD OUR LATEST EBOOK >>>
DOWNLOAD OUR LATEST EBOOK >>>
In this eBook, you will learn:
- The newest and growing trends in cybersecurity tools, processes,
and data storage. - Major cyber attacks that occurred in 2021, their impact, and what
we can learn. - Our expectations for what cybersecurity will look like in 2022,
based on the data collections and observations from Avertium
security experts, as well as commentary from Avertium's partners. - The tools and services your organization needs to show no
weakness in 2022.