
Case Study:
INTERNOVA TRAVEL GROUP
Discover how Avertium helps unburden Internova Travel Group's security team to have the space to start focusing on more strategic cybersecurity priorities.
Cadet Blizzard, a newly identified Russian threat actor, was observed by researchers in January 2022 and is believed to be associated with the General Staff Main Intelligence Directorate (GRU). While their activities were initially observed during the targeting of Ukraine using the WhisperGate wiper malware, there are indications that the group has been operational since at least 2020.
Avertium’s security partner, Microsoft, has successfully tracked the threat actor and initially referred to the group as DEV-0586 before officially naming them Cadet Blizzard. Known for their disruptive and destructive attacks, Cadet Blizzard has a haphazard approach to their operations, using any available means to collect information, cause disruptions, and destroy data.
Despite their tendency for destruction, Cadet Blizzard appears to demonstrate a lower level of operational security compared to more established Russian threat groups like Forest Blizzard and Seashell Blizzard. The group focuses their operations on espionage, information operations, and destructive attacks primarily targeting entities within Ukraine, Europe, Central Asia, Latin America, as well as NATO member states providing military aid to Ukraine. Let’s examine Cadet Blizzard, their tactics and techniques, and how organizations can remain vigilant in protecting themselves against the threat actor.
In operation since 2020, Microsoft suspects the Russian threat actor, Cadet Blizzard is linked to the Russian GRU and operates independently of other GRU-related groups. The threat actor is connected to the defacement of numerous Ukrainian organization websites, along with multiple operations involving the hack-and-leak Telegram channel called "Free Civilian".
Cadet Blizzard primarily targets government organizations and IT providers in Ukraine, occasionally expanding its operations to Europe and Latin America. The group’s attacks have focused on IT service providers, emergency services, government organizations, law enforcement, and non-profit organizations. Although targets are primarily located in Ukraine, the group has also targeted NATO member states that provide military aid to Ukraine.
In January 2022, Cadet Blizzard emerged as a threat actor engaged in destructive cyber operations. They employed a new wiper malware called WhisperGate (also known as PAYWIPE), which caused significant damage to Ukraine’s systems and networks. These attacks occurred during the period leading up to Russia's military invasion of the country.
Avertium published a Threat Intelligence Report regarding WhisperGate and how it impacted the U.S. and Ukraine. WhisperGate is malware that was discovered in January 2022 and was designed to look like ransomware but lacked the ransom recovery mechanism. The malware had two stages and was noted to be similar to NotPetya but with more capabilities. WhisperGate impacted the Ukraine Foreign Ministry, the Ministry of Education and Science, and other state services in Ukraine.
Cadet Blizzard typically infiltrates and controls compromised networks for extended periods, frequently exfiltrating data before engaging in disruptive actions. Their most active period occurred from January to June 2022, followed by a period of decreased activity. However, the group reemerged in January 2023 with strengthened attacks on various targets in Ukraine and Europe, including a fresh wave of website defacements.
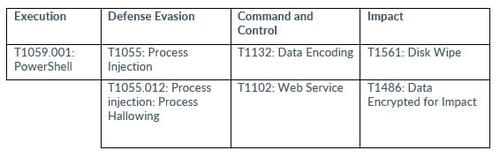
Interestingly, Cadet Blizzard conducts their operations during their targets’ non-business hours, making their activity less likely to be detected, making states involved in providing military aid to Ukraine are at greater risk. The threat actor mainly gains initial access by exploiting vulnerabilities in web servers, Confluence servers (CVE-2021-26084) and Exchange servers (CVE-2022-41040 and ProxyShell).
Also, Cadet Blizzard might exploit common vulnerabilities found in different open-source platforms, including content management systems. The group adheres to conventional network operator practices, frequently utilizing "living-off-the-land" strategies to navigate networks, gather passwords and sensitive data, and employ evasion techniques and persistence mechanisms to maintain access after an initial breach.
Cadet Blizzard maintains persistence on targeted networks by employing common web shells for command and tunneling purposes. They use web shells such as P0wnyshell, reGeorg, PAS, and even custom versions found in publicly accessible exploit kits. In February 2023, CERT-UA detected an attack on a Ukrainian state information system. The attack involved a variant of the PAS web shell, which is believed to be exclusive to Cadet Blizzard operations during that time.
To carry out offline credential harvesting, the Russian threat actor uses Sysinternals tools like procdump to dump LSASS. They often rename procdump64 to different names, such as dump64.exe. Also, Cadet Blizzard extracts registry hives using native methods, specifically through reg save. Lateral movement is conducted with valid network credentials obtained via credential harvesting.
Cadet Blizzard has been observed utilizing the Win32_NTEventlogFile commandlet in PowerShell to extract system and security event logs to a designated directory. These actions are believed to be part of their anti-forensics measures. The typical files targeted during the extraction process include:
During their operational phases, Cadet Blizzard frequently deletes the files they use for lateral movement. To disable Microsoft Defender Antivirus, the threat actor’s malware implants employ various methods, including:
Cadet Blizzard's operations are not isolated. There are significant signs of their involvement with other malicious cyber activities that may have a wider reach or connections beyond Russia. At times, they have used services linked to these cyber ecosystems, like Storm-0587. Storm-0587 is a cluster of activity that started in April 2021. It involves the use of weaponized documents distributed in phishing campaigns. These documents contained downloaders and document stealers.
One notable tool used by Storm-0587 is SaintBot, a less common downloader that often appears in targeted phishing emails. SaintBot can be customized to deliver various types of payloads. In Ukraine, this malware variant often deploys a version of an AutoIT information stealer called OUTSTEEL. OUTSTEEL collects specific documents on the infected machine that the threat actors find valuable.
Additionally, Cadet Blizzard has also received support from at least one private sector organization within Russia that aids their activities. This information implies that Cadet Blizzard may have affiliations or collaborations with other entities in their operations.
While Cadet Blizzard's primary focus appears to be on targeting Ukraine, their operations are not limited to this region. They have also launched attacks in various other parts of Europe, Central Asia, and even Latin America. Previously, Avertium reported that the cyber conflict between Russia and Ukraine would escalate in the near future.
Both Recorded Future and Google's TAG (Threat Analysis Group) warned that Russia had plans to intensify cyber attacks against Ukraine. Google's TAG team expressed high confidence that if the war shifts significantly in favor of Ukraine, Moscow will increase disruptive and destructive attacks throughout 2023. There are predictions that Russian hacktivist groups would support Russia's military advancements against Ukraine, potentially extending the cyber warfare into regions (including NATO countries) that Russia has not been able to infiltrate through physical means.
Similar to the Russian Advanced Persistent Threat (APT) group Winter Vivern, Cadet Blizzard is another Russian APT that has reappeared after a period of reduced activity - targeting government websites and exploiting well-known vulnerabilities. According to the acting deputy head of the Security Service of Ukraine's (SSU) Cybersecurity Department, Moscow was responsible for nearly 1,200 cyberattacks and significant cyber incidents in the first quarter of 2023. Based on this trend, it was estimated that Russia may carry out around 4,800 attacks this year, surpassing the number of cyberattacks attributed to Russian threat actors in 2022 by approximately 300. The increased targeting by Russia highlights the spillover risk, emphasizing the importance for organizations and security professionals worldwide to strengthen their digital defenses.
SHA256
IPV4
Domain
MD5
Related Resource:
Cadet Blizzard emerges as a novel and distinct Russian threat actor | Microsoft Security Blog
Cadet Blizzard emerges as a novel and distinct Russian threat actor | Microsoft Security Blog
How WhisperGate Affects the U.S. and Ukraine (avertium.com)
Targeted Phishing Attack against Ukraine Government Expands to Georgia (intezer.com)
Russian APT 'Cadet Blizzard' Behind Ukraine Wiper Attacks (darkreading.com)
APT Winter Vivern Resurfaces (avertium.com)
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.