Ragnar Locker Ransomware (Everything You Need To Know)
Executive Summary of ragnar locker ransomware
Initially discovered in April 2020, Ragnar Locker is both ransomware and a ransomware gang. The threat actor has been on the Federal Bureau of Investigation's (FBI) radar since the gang breached 52 organizations across 10 critical infrastructure sectors. The critical industries that Ragnar Locker has breached include energy, manufacturing, financial services, government, and information technology.
Ragnar Locker is known for constantly switching up their obfuscation techniques to avoid detection and prevention, as well as deterring organizations from contacting law enforcement after a breach. Let’s take a look at Ragnar Locker’s tactics and techniques, and why it’s important to remember the dangers of paying the demanded ransom.
about ragnar locker
Although Ragnar Locker was discovered by the FBI in April 2020, the group has actually been active since December 2019. Ragnar Locker is both the name of the ransomware group and the name of the ransomware. The gang works as a part of a ransomware family, which means they are associated with several ransomware variants or threat actor groups.
Ragnar Locker is known for using the double extortion tactic, which involves threat actors exfiltrating sensitive data, then triggering the encryption attack, and ultimately threatening to leak the data if the demanded ransom isn’t paid. To avoid prevention and detection, the threat actor frequently changes their obfuscation techniques.
Techniques and tactics
Ragnar Locker initiates their attacks by compromising the networks of companies through RDP service – using brute force to guess passwords or using stolen credentials purchased on the dark web. After compromising their target’s network, the threat actor elevates their privileges by exploiting CVE-2017-0213 found in Windows COM Aggregate Marshaler. According to Microsoft, CVE-2017-0213 is an elevation of privilege that allows attackers to run arbitrary code with elevated privileges. To exploit the vulnerability, the attacker runs a specially crafted application.
According to Acronis, to evade detection, Ragnar Locker will sometimes deploy a VirtualBox virtual machine (VM) with a Windows XP image – this is done to run the ransomware encryption attack (a technique adopted by Maze ransomware operators). Next, the image is loaded to the VirtualBox virtual machine, which maps all local drives as read/writable into the virtual machine. As a result, the ransomware process is able to run inside the VM to encrypt files. The host files recognize the encryption as a trusted VirtualBox process, which means that many security products will be ignored.
Next, Ragnar Locker deletes shadow copies and disables antivirus countermeasures, followed by using a PowerShell script to move from one company network to another. Before the ransomware is deployed, Ragnar Locker steals files and uploads them to servers before publishing them – this is done just in case their victim refuses to pay the demanded ransom. Obfuscation techniques protect the ransomware code, and those techniques include adding junk code in addition to encryption. The locale information is checked to avoid CIS countries from being infected.
Crypto keys and obfuscated configuration strings are stored in a payload PE file, which contains a section named “.keys”. The hardcoded obfuscated strings are decrypted in runtime and the first decrypted value is a unique sample ID. Strings related to backup and antivirus solutions are terminated, including Sophos and Veeam. Ragnar Locker also terminates remote management software tools such as Kaseya and ConnectWise, allowing the threat actor to evade detection and ensuring remotely logged-in admins don’t prevent the ransomware deployment process.
Remote management software is used by managed service providers (MSPs).
Additionally, Ragnar Locker leaves a ransomware note behind which provides the address of their leak site, live chat, and Ragnar Secret, which is a ‘company_id’ encoded with Base64. Ragnar Locker’s stolen data is published to their data leak site from the victim’s corporate network before running Ragnar Locker due to the ransomware not having network communication.
Salsa20 Encryption
Interestingly, Ragnar Locker uses a Salsa20 encryption algorithm with a custom matrix. The matrix includes generated keys (placed in rearranged order) and is 64 bytes in size, with 8 bytes defining the stream position. Removing 16 bytes from the second key, Ragnar Locker leaves the stream position values with zero bytes. The encrypted Salsa20 key data can be found in the encrypted file, with the signature _RAGNAR_ added to the footer.
In August 2021, Avertium published a Threat Intelligence Report featuring BlackMatter ransomware. Like Ragnar Locker, the threat actor used a custom Salsa20 encryption algorithm in their attack against Kaseya. The ransomware gang, DarkSide also used a custom Salsa20 encryption algorithm.
BlackMatter began making its presence known as a ransomware-as-a-service (RaaS) gang in July 2021, claiming to be a combination of the best qualities of DarkSide and REvil – two ransomware groups that are now defunct. There was also speculation that BlackMatter was a rebrand of DarkSide and REvil because BlackMatter has utilized some of DarkSide and REvil’s tactics. DarkSide was responsible for the attack on the Colonial Pipeline, while REvil was responsible for the devastating attack on Kaseya.
 Image 1: Initial State of Salsa20 (Source: Wikipedia.com)
Image 1: Initial State of Salsa20 (Source: Wikipedia.com)
While there is no observed direct link between Ragnar Locker, DarkSide, and BlackMatter, it’s important to note that the three groups are using custom Salsa20 encryption algorithms. One of two things is possible – because ransomware gangs like BlackMatter were so successful in the past, more ransomware gangs are starting to use custom Salsa20 encryption algorithms, or there is an undiscovered link between Ragnar Locker, BlackMatter, and DarkSide.
ragnar locker attacks
In November 2021, the video game giant, Capcom was breached by Ragnar Locker. The ransomware attack affected the company’s email and file servers and encrypted 1 TB of data. Capcom is a Japanese video game developer known for several multi-million-dollar game franchises, including Street Fighter and Resident Evil.
Capcom discovered their breach on November 2, 2021, and confirmed that the attack happened due to unauthorized access by a third party. Later in the month, the company confirmed that personal and corporate information (data of former employees, shareholders, store members, and website members) was compromised as well.
In addition to Capcom, Ragnar Locker attacked the North American network of Energias de Portugal in April 2021. The gang ended up stealing 10 TB of sensitive company / customer data and insisted on a ransom demand of 1,580 Bitcoin, which is the equivalent of $11 million. Ragnar Locker was also responsible for breaching the Italian liquor company, Campari Group.
Campari Group is known for their popular liquor brands, including SKYY Vodka, Wild Turkey, and Grand Marnier. On November 1, 2020, the threat actors stole 2 TB of unencrypted files and demanded a $15 million (in Bitcoin) ransom to recover the files. The files included bank statements, contractual agreements, emails, and much more. In December 2020, Ragnar Locker attacked the aviation giant, Dassault Falcon Jet, which is a subsidiary of the French aerospace company Dassault Aviation.
FBI warning – agriculture
In April 2022, the FBI warned Food and Agriculture (FA) sector organizations that there is an increased risk of ransomware attacks that are more likely to take place during the harvest and planting seasons. Ransomware gangs target the U.S. constantly, but the FBI was concerned about several groups and possible attacks against FA organizations during critical seasons. The groups include BlackByte, Ragnar Locker, and Avoslocker – all having breached dozens of U.S. critical infrastructure.
The FBI is particularly concerned about attacks during the harvest and planting season because the attacks could lead to operation disruptions and have a negative impact on the global food supply chain. During the fall of 2021, there were ransomware attacks against six-grain cooperatives and two attacks in early 2022. The attacks could have impacted the planting season and disrupted the supply of seeds and fertilizer.
Attacking the agriculture sector is appealing to threat actors because they know that their targets will be more willing to pay the demanded ransom due to the time-sensitive nature of agriculture production. Take a look at the ransomware attacks that disrupted the operations of agriculture in recent years according to the FBI:
- In March 2022, a multi-state grain company suffered a LockBit 2.0 ransomware attack. In addition to grain processing, the company provides seed, fertilizer, and logistics services, which are critical during the spring planting season.
- In February 2022, a company providing feed milling and other agricultural services reported two instances in which an unauthorized actor gained access to some of its systems and may have attempted to initiate a ransomware attack. The attempts were detected and stopped before encryption occurred.
- Between 15 September and 6 October 2021, six-grain cooperatives experienced ransomware attacks. A variety of ransomware variants were used, including Conti, BlackMatter, Suncrypt, Sodinokibi, and BlackByte. Some targeted entities had to completely halt production while others lost administrative functions.
- In July 2021, a business management software company found malicious activity on its network, which was later identified as HelloKitty/Five Hands ransomware. The threat actor demanded a $30 million USD ransom. The ransomware attack on the company led to secondary ransomware infections on a number of its clients, which included several agricultural cooperatives.
These kinds of attacks could impact the entire food chain. Grain is not just consumed by humans, but by animals as well. Also, significant disruption of corn and grain production will also impact commodities trading and stocks. The International Grains Council has already forecasted that global corn production will drop by 13 million tons in 2022-2023. Critical infrastructure attacks by ransomware gangs don’t just cost organizations time and money, they could cost the world its food supply.
don't pay the ransom
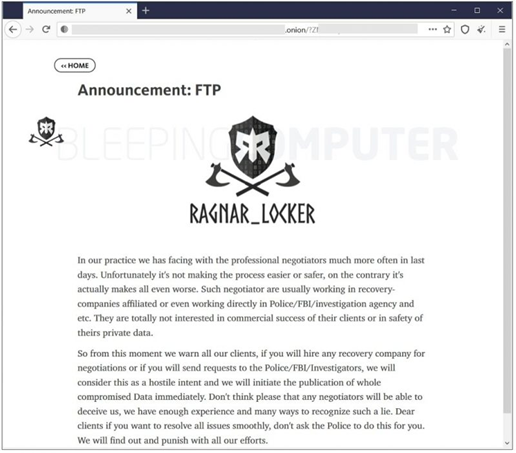
Image 2: Ragnar Locker's Warning
Ragnar Locker makes threats against organizations that contact the FBI and heavily encourages their victims to stay quiet. Their letter above states that contacting the FBI doesn’t make the negotiating process safe or easy. They also stated that negotiation companies often work directly with the FBI, so they discourage victims from reaching out to them as well. If victims contact either, the ransomware gang will consider it “hostile intent” and will publish their victims’ stolen data immediately. Ragnar Locker also makes it clear that if you contact law enforcement or a data recovery company and lie to them about it, they’ll know and will act accordingly.
Although Ragnar Locker makes some pretty strong and aggressive threats, the FBI discourages organizations from paying the ransom. Their warning stated that paying a ransom only encourages threat actors to target additional organizations and gives the green light for other cyber criminals to continue to distribute ransomware. Paying the ransom also helps fund the adversary’s illicit activities.
After being breached, most organizations panic and try to keep their breach under wraps by quietly negotiating a ransom payment. Sometimes, they will use a negotiation service company to help them with this feat. However, Coveware, a ransomware negotiation company, has found that ransomware gangs aren’t staying true to their word, and they are increasingly not deleting stolen data after ransoms are paid.
While it’s understood that your business operations may be disrupted or even be completely non-functioning, it’s always best to report ransomware incidents to the FBI immediately. The FBI has investigators and analysts, and they need critical information to help track the ransomware attackers, hold them accountable, and prevent future attacks. Field office contacts can be located at http://www.fbi.gov/contact-us/field-offices.
How Avertium is Protecting Our CUSTOMERS
Even with anti-malware solutions installed, Ragnar Locker is a great risk to organizations. As you can see, the Ragnar Locker ransomware gang uses advanced defense-evasion techniques to bypass anti-virus software. However, Avertium has advanced services that can help keep your organization safe:
- Avertium recommends utilizing our service for DFIR (Digital Forensics and Incident Response) to help you rapidly assess, contain, eradicate, and recover from a security incident like a malware attack.
- Implement XDR as a prevention method. Our XDR is a combination of monitoring software like LogRhythm, Microsoft Azure Sentinel, or AlienVault, combined with endpoint protection such as SentinelOne. XDR platforms enable cybersecurity through a technology focus by collecting, correlating, and analyzing event data from any source on the network. This includes endpoints, applications, network devices, and user interactions.
- MDR provides an in-depth investigation into potential threats to an organization’s network. Avertium’s risk-based approach to managed security delivers the right combination of technology, field-validated threat intelligence, and resource empowerment to reduce complexity, streamline operations, and enhance cybersecurity resilience. If you need a more advanced security solution, MDR is the next step. MDR is an outsourced security control solution that includes the elements of EDR, enhanced with a range of fundamental security processes.
- Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
Avertium’s Recommendations
Avertium and the FBI recommend the following for mitigation against Ragnar Locker ransomware:
- Back-up critical data offline.
- Ensure copies of critical data are in the cloud or on an external hard drive or storage device. This information should not be accessible from the compromised network.
- Secure your back-ups and ensure data is not accessible for modification or deletion from the system where the data resides.
- Use multi-factor authentication with strong passwords, including for remote access services.
- Keep computers, devices, and applications patched and up to date.
- Monitor cyber threat reporting regarding the publication of compromised VPN login credentials and change passwords and settings.
- Consider adding an email banner to emails received from outside your organization.
- Disable unused remote access/Remote Desktop Protocol (RDP) ports and monitor remote access/RDP logs.
- Audit user accounts with administrative privileges and configure access controls with least privilege in mind.
- Implement network segmentation.
Avertium and the FBI recommend the following guidelines for general ransomware attacks:
- Regularly back up data, air gap, and password-protect backup copies offline. Ensure copies of critical data are not accessible for modification or deletion from the system where the data resides.
- Implement a recovery plan that includes maintaining and retaining multiple copies of sensitive or proprietary data and servers in a physically separate, segmented, secure location (i.e., hard drive, storage device, the cloud).
- Identify critical functions and develop an operations plan in the event that systems go offline. Think about ways to operate manually if it becomes necessary.
- Implement network segmentation.
- Install updates/patch operating systems, software, and firmware as soon as they are released.
- Use multi-factor authentication where possible.
- Use strong passwords and regularly change passwords to network systems and accounts, implementing the shortest acceptable timeframe for password changes. Avoid reusing passwords for multiple accounts and use strong passphrases where possible.
- Disable unused remote access/RDP ports and monitor remote access/RDP logs.
- Require administrator credentials to install software.
- Audit user accounts with administrative or elevated privileges and configures access controls with the least privilege in mind.
- Install and regularly update anti-virus and anti-malware software on all hosts.
- Only use secure networks and avoid using public Wi-Fi networks. Consider installing and using a virtual private network (VPN).
- Consider adding an email banner to messages coming from outside your organization.
- Focus on cyber security awareness and training. Regularly provide users with training on information security principles and techniques as well as overall emerging cybersecurity risks and vulnerabilities (i.e., ransomware and phishing scams).
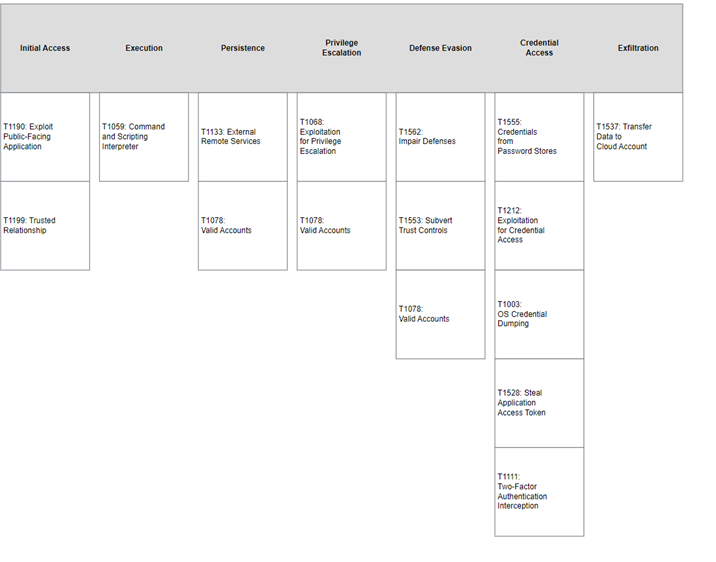
MITRE Map
Indicators of Compromise (IoCs)
- ShingXuan7110@protonmail[.com]
- scanjikoon@yahoo[.com]
- alexeyberdin17@gmail[.com]
- titan_fall572cool@gmail[.com]
- Vivopsalrozor@yahoo[.com]
- Gamarjoba@mail[.com]
- shadow98@gmail[.com]
- shawn.brown2@gmail[.com]
- Alexey_Berdin@list[.ru]
- sh0d44n@gmail[.com]
- alexeyberdin437@gmail[.com]
- alexeyberdin38@gmail[.com]
- alexeyberbi@gmail[.com]
Bitcoin Addresses
- 19kcqKevFZhiX7NFLa5wAw4JBjWLcpwp3e
- 21CG8RAqNaJCrmEdVLK7mm2mTuuK28dkzCU
- 151Ls8urp6e2D1oXjEQAkvqogSn3TS8pp6
IP Addresses
- 25.93[.106]
- 146.164[.193]
- 40.10[.25]
- 45.65[.52]
- 141.160[.43]
- 63.89[.250]
- 211.254[.181]
- 44.236[.38]
- 120.238[.107]
- 216.196[.181]
- 55.38[.44]
- 203.132[.32]
- 12.212[.231]
- 42.39[.10]
- 111.153[.24]
- 32.222[.98]
- 227.202[.72]
- 89.95[.163]
- 35.60[.92]
- 26.193[.165]
File Hashes
- 6d122b4bfab5e75f3ae903805cbbc641
- 68eb2d2d7866775d6bf106a914281491d23769a9eda88fc078328150b8432bb3
- 6360b252b21fe015d667b093f6497e33
- 1de475e958d7a49ebf4dc342f772781a97ae49c834d9d7235546737150c56a9c
- ragnar_{computer_id}
- .keys
- RGNR_{computer_id}.txt
Websites
- [http://my]kgoj7uvqtgl367.onion/client/?6bECA2b2AFFfBC1Dff0aa0EaaAd468bec0903b5e4Ea58ecde3C264bC55c7389E
- [http://p6]o7m73ujalhgkiv.onion/?page_id=171
- [http://rg]leaktxuey67yrgspmhvtnrqtgogur35lwdrup4d3igtbm3pupc4lyd..onion/
- [http://rg]leak7op734elep..onion/
Supporting Documentation
Threat Actor Profile – “BlackMatter” Ransomware (avertium.com)
Analysis of Ragnar Locker Ransomware (acronis.com)
FBI Warns of Cyberattacks and Production Drop Forecast for Corn - AG INFORMATION NETWORK OF THE WEST
Ragnar Locker Gang Warns Victims Not to Call the FBI | Threatpost
CVE-2017-0213 - Security Update Guide - Microsoft - Windows COM Elevation of Privilege Vulnerability
Ransom.Ragnar | Malwarebytes Labs | Detections
Campari hit by Ragnar Locker Ransomware, $15 million demanded (bleepingcomputer.com)
Microsoft Word - PIN-20220420-001 TLP_WHITE (ic3.gov)
FBI warns of ransomware attacks targeting United States agriculture sector (bleepingcomputer.com)
Gaming Giant Capcom Hit By Ragnar Locker Ransomware: Report | Threatpost
FBI: Ransomware gang breached 52 United S critical infrastructure orgs (bleepingcomputer.com)
BlackMatter Ransomware Analysis; The Dark Side Returns (trellix.com)
FBI issues IoCs to help organizations defend against RagnarLocker ransomware (scmagazine.com)
Microsoft Word - PIN-20220420-001 TLP_WHITE (ic3.gov)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.
Related Resource: [Threat Report] An In-Depth Look at Data Extortion Group, Lapsus$