MGM/Caesars Post-Mortem and Attribution
executive summary
In a recent cyber security incident that sent shockwaves through the industry, MGM Resorts International's resorts and casinos across the U.S. were plunged into chaos by a sophisticated cyber attack. Initially believed to be the work of the notorious group known as Scattered Spider, this operation showcased an expertise in impersonation and malware deployment.
As we dive into the details, it becomes clear that this attack began with a clever social engineering breach of the company's IT help desk—a stark reminder of the ever-evolving tactics employed by threat actors. In this report, we explore the details of the attack, as well as which threat group may have been responsible for the attack on MGM.
tir snapshot
- On September 10, 2023, a cyberattack led the Las Vegas-based company, MGM Resorts International, to shut down certain systems, resulting in the disruption of digital room keys, requiring manual payouts for slot machines, and causing outages in websites and online reservation systems.
- By September 13, 2023, reports surfaced that things were becoming dire for the company, as it was projecting to lose up to $8.4 million in revenue per day as the cybersecurity issues were being resolved.
- When reports initially surfaced, the breach was attributed Scattered Spider, which uses ransomware from ALPHV, also known as BlackCat, a ransomware-as-a-service (RaaS) operation.
- Scattered Spider excels in social engineering, a tactic involving the manipulation of victims by impersonating individuals or entities with whom the victim has a connection.
- It was later revealed by BlackCat (ALPHV) that one of their affiliates was in fact responsible for the MGM attack, but they did not specifically name Scattered Spider (although well-versed researchers are almost certain they are the culprits).
- Also, during this time, Scattered Spider infiltrated Caesars Entertainment's network. Caesars Entertainment hinted at the possibility of paying the attacker to prevent the release of customer data stolen during the attack, with the ransom demand reportedly set at $30 million.
- Now, after more than 10 days, MGM's systems are back online, and hotel reservations are available through the company's mobile app and website.
- MGM Resorts and Caesars Entertainment have both submitted mandatory disclosures to the Securities and Exchange Commission (SEC) following the ransomware attacks on their casino operations.
- Caesars' SEC filing, dated September 14, acknowledges an unauthorized entity accessed and copied the company's loyalty program database on September 7. However, there is limited detail regarding MGM's filing, and the SEC has not responded to requests for comments.
the attack on mgm
On September 10, 2023, a cyberattack led the Las Vegas-based company, MGM Resorts International, to shut down certain systems, resulting in the disruption of digital room keys, requiring manual payouts for slot machines, and causing outages in websites and online reservation systems.
On September 11, 2023, according to reports, one of the company's properties, the Bellagio Las Vegas, confirmed that computer systems at all resorts were experiencing downtime, leading to a manual operation of computer-based tasks. Staff at the resort also mentioned that the interruption had an impact on credit card machines throughout their properties. When attempting to access mgmresorts.com, a message appeared, stating, "The MGM Resorts website is presently unavailable."
Across their social media platforms, MGM issued a statement addressing the technical challenges they were confronting.
Image 1: MGM's Statement About Their Breach on X (formerly known as Twitter)
By September 13, 2023, reports surfaced that things were becoming dire for the company, as it was projecting to lose up to $8.4 million in revenue per day as the cybersecurity issues were being resolved. The casino has 19 casino hotels (with more than 40,000 rooms), one of which is in the casino capital of the world, Las Vegas.
A study conducted by David Katz, a gaming industry analyst at Jeffries, indicated that MGM Resorts International was projected to experience a short-term decline in both revenue and cash flow, ranging from 10% to 20%, "as long as the existing conditions persist." Furthermore, Jefferies analysts disclosed that the corporation generates a daily revenue of $42 million and a daily cash flow of $8 million across its entire enterprise.
OTHER STORIES
According to the Financial Times, initial reports stated threat actors tried to manipulate MGM’s slot machines but resorted to a ransomware attack when their initial plan failed. The attempt to manipulate MGM's slot machines likely failed due to the attackers' lack of familiarity with the underlying code, as noted by Lior Frenkel, CEO of Israel-based cybersecurity provider Waterfall. This difficulty arose because the threat actors employ a generic toolkit designed to target a broad range of companies, regardless of their specific industry.
attribution and tactics
ATTRIBUTION
When reports initially surfaced, the breach was attributed to Scattered Spider, which uses ransomware from ALPHV, also known as BlackCat, a ransomware-as-a-service (RaaS) operation. Scattered Spider excels in social engineering, a tactic involving the manipulation of victims by impersonating individuals or entities with whom the victim has a connection. Their expertise lies in "vishing," the art of accessing systems through persuasive phone calls.
Members of Scattered Spider, believed to be in their late teens and early 20s, are presumed to be located in Europe, with a possibility of some being in the US. They are fluent in English, which enhances the credibility of their vishing endeavors.
It was later revealed by BlackCat (ALPHV) that one of their affiliates was in fact responsible for the MGM attack, but they did not specifically name Scattered Spider. They did however, report to Bleeping Computer that the affiliate responsible was not the same threat actor that attacked Western Digital in March 2023.
Following MGM’s internal infrastructure shutdown, the threat actors encrypted over 100 ESXi hypervisors. The group stated that they had exfiltrated data from MGM's network and still maintained access to parts of the company's infrastructure. Additionally, the threat actors encrypted MGM's data and demanded cryptocurrency for its release. They issued a threat of launching additional attacks unless an agreement to pay a ransom was reached.
According to sources well-versed in the matter, online reports later identified the threat actor behind the MGM Resorts breach as Scattered Spider (Crowdstrike), although various cybersecurity firms have adopted different names to track this same threat actor, such as "0ktapus" (Group-IB), "UNC3944" (Mandiant), and "Scatter Swine" (Okta).
The attribution of the MGM breach is somewhat complex, with BlackCat, a Ransomware-as-a-Service (RaaS) operation, making public claims of responsibility, while Scattered Spider, known to utilize BlackCat's malware, is also linked to the incident, leading to potential confusion in assigning blame. While the claims by Scattered Spider or BlackCat can't be independently verified, security researchers noted similarities with attacks by Scattered Spider on over 100 other victims in the past two years.
TACTICS
In MGM’s case, the threat actors discovered an employee's details on LinkedIn and then proceeded to impersonate that individual when contacting MGM's IT help desk – the help desk call lasted 10 minutes. Their objective was to secure the necessary credentials for gaining access to and infecting the company’s systems. A follow-up report from Bloomberg, noted that Okta, a service provider for MGM, had been actively supporting MGM in the aftermath of the incident.
Image 2: A Post (formerly known as a Tweet) from VX-Underground
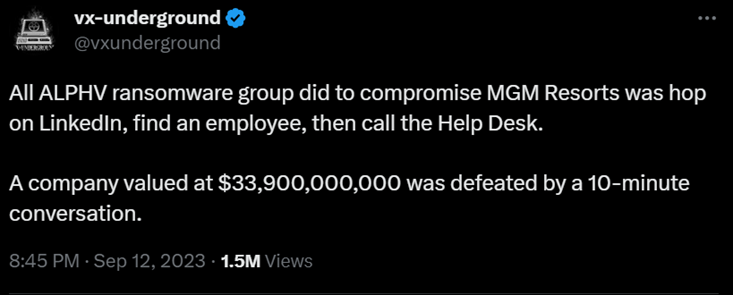
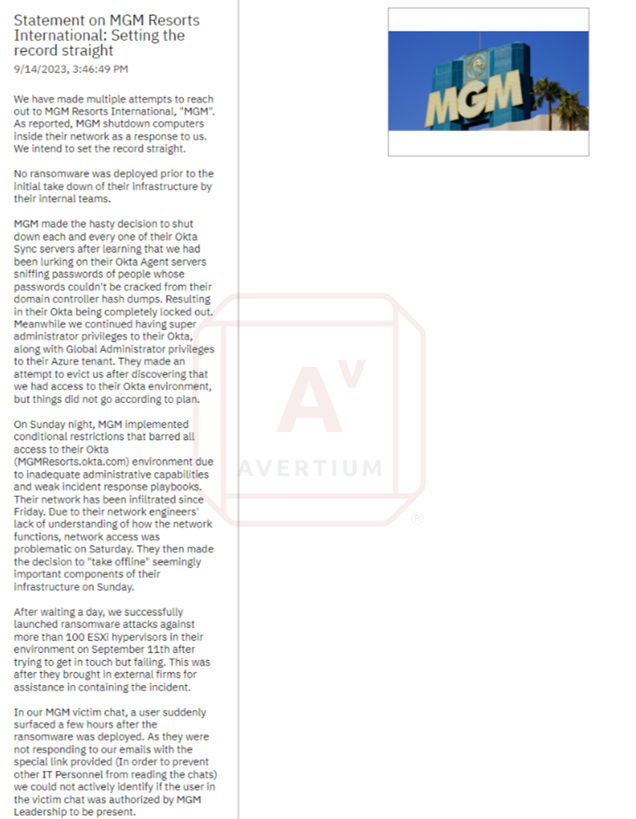
Despite MGM's efforts to shut down the Okta servers for synchronization, the threat actors stayed within the network, as stated in BlackCat's announcement. They maintained that they still possessed super administrator privileges within MGM's Okta environment and held Global Administrator permissions for the company's Azure tenant.
Observing MGM's response, which involved showing no inclination to engage in negotiations through the provided chat, the threat actors proceeded to launch the ransomware attack. During this time, the threat actors admitted they were uncertain about the specific nature of the data they acquired from MGM. However, they did threaten to extract sensitive information and make it public unless negations were made.
Image 3: BlackCat Releases Statement Regarding MGM Attack on Tor Site
Additionally, Bloomberg reporters disclosed that Scattered Spider also infiltrated Caesars Entertainment's network. Caesars Entertainment hinted at the possibility of paying the threat actor to prevent the release of customer data stolen during the attack, with the ransom demand reportedly set at $30 million. By September 19, 2023, Caesars ended up paying the threat actors $15 million in ransom.
In a recent statement, BlackCat noted that MGM Resorts had not responded through the provided communication channel, indicating a reluctance to negotiate a ransom payment. The hackers highlighted that MGM's only response to the breach had been to disconnect "each and every one of their Okta Sync servers" after discovering the intrusion, as they were attempting to capture any passwords that had not been retrieved from the domain controller hash dumps.
CURRENTLY
Now, after more than 10 days, MGM’s systems are back online and hotel reservations are available through the company’s mobile app and website. However, there are still gaming machines at some properties that are still down. The attack is still under investigation by law enforcement, and there is no further information regarding when or if a ransom was paid by the company.
Image 4: MGM's Most Recent Update on X (formerly Twitter)
about scattered spider
Scattered Spider, a threat group, was previously known to target the telecom and business process outsourcing sectors with a focus on infiltrating mobile carrier networks. Recently, their activities escalated significantly, primarily impacting the United States, the United Kingdom, Germany, France, Italy, Canada, Australia, and Japan.
Between June 2022 and the winter months, security researchers observed five intrusions by Scattered Spider. In December 2022, their campaign aimed to breach telecom systems, access subscriber data, and conduct SIM swapping. They exploited a vulnerability in ForgeRock AM server to elevate their privileges on an AWS instance, often using compromised AWS tokens.
Scattered Spider often initiates access through social engineering, employing phone calls, SMS, or Telegram messages to impersonate IT staff. Victims are led to fake websites or prompted to download Remote Monitoring and Management tools, granting remote control to the threat actor. Even when Multi-Factor Authentication (MFA) is active, Scattered Spider uses various techniques to compromise victims.
The threat actors target a broad range of environments across industries, using tools such as AnyDesk, TeamViewer, and SSH RevShell. Scattered Spider downloads additional tools from various sources and accesses SharePoint and OneDrive for sensitive information. They even exploited an old kernel vulnerability for privilege escalation and evading detection by security systems. Scattered Spider's tactics emphasize the evolving and persistent nature of cyber threats in today's digital landscape.
the sec
MGM Resorts and Caesars Entertainment have both submitted mandatory disclosures to the Securities and Exchange Commission (SEC) following ransomware attacks on their casino operations. In March of last year, the SEC enacted new regulations requiring publicly traded companies to report significant cybersecurity incidents to the regulatory body within a four-day window.
Caesars' SEC filing, dated September 14, acknowledges an unauthorized entity accessed and copied the company's loyalty program database on September 7. This database contained sensitive information, including Social Security and driver's license numbers, for a "significant" number of members.
MGM Resorts’ SEC report (dated September 13, 2023) is limited in detail. The hospitality company reiterates its earlier press release from September 12, 2023 indicating the presence of a "cybersecurity issue" and an ongoing investigation. Caesars informed the SEC that, "Our customer-facing operations, including our physical properties and our online and mobile gaming applications, have not been impacted by this incident and continue without disruption."
“We have incurred, and may continue to incur, certain expenses related to this attack, including expenses to respond to, remediate, and investigate this matter. The full extent of the costs and associated consequences of this incident, including potential coverage by our cybersecurity insurance or potential indemnification claims against third parties, remains undetermined." – Caesars
The SEC has chosen not to comment on the disclosure filings.
conclusion
The breaches targeting MGM and Caesars Entertainment highlight the persistent nature of modern cyber threats. Scattered Spider seems to target vulnerabilities indiscriminately across various industries, rather than focusing on a specific sector. They exploit any vulnerability they come across.
Their adaptable tactics, including social engineering, demonstrate their ability to infiltrate high-profile organizations. Their fluency in English is what distinguishes them from other ransomware groups, enabling them to evade detection and execute successful social engineering attacks. Let these incidents serve as a reminder of the importance of remaining vigilant and adhering to robust cybersecurity best practices.
avertium's recommendations
Please Note: The subsequent guidelines are based on CrowdStrike's comprehensive list of security controls for Scattered Spider, and we strongly advise their implementation.
MFA
- Layered MFA adds a phone call or text message to password-based authentication. Layered MFA may deter attacks, but attacks can still use MFA fatigue to penetrate those defenses. Modern, passwordless authentication methods such as Windows Hello, FIDO, or Microsoft Authenticator will effectively defend against MFA fatigue and advanced adversary-in-the-middle attacks.
- Avoid unsupervised MFA self-enrollment or reset and disallow any self-enrollment from external IP space.
- Allow only one trusted MFA device per user.
- Implement a global password reset and KRBTGT account reset twice per domain if compromise is suspected.
Monitoring
- Utilize custom rules and queries to identify compromised or vulnerable accounts and credentials, enhancing the ability to spot potential threats.
- Regularly review and monitor the health of Active Directory, paying attention to newly created accounts, changes to group memberships, and re-enabled accounts.
- Make use of the Protected Users Security Group in Active Directory to protect privileged accounts from NTLM (NT LAN Manager) usage, reducing security risks.
- Enable real-time alerting mechanisms to promptly detect and respond to known compromised credentials, enhancing the organization's security posture.
- Set up custom indicators of attack (IOAs) to configure alerts and blocks for any unauthorized or abnormal Remote Monitoring and Management (RMM) tools. This step is crucial since threat actors have demonstrated the use of a diverse range of RMM tools in their activities during previous investigations.
AWS Token Pivoting
- Ensure IMDSv2 is enabled on all EC2 instances to the extent possible (Note: Some products might still lack support for v2).
- Enable GuardDuty in all active regions (GuardDuty includes detections for abuse of EC2 instance credentials beyond an EC2 instance).
- Deprecate static IAM user access keys where applicable, favoring IAM roles instead.
Enforce Azure Conditional Access Policies (CAP):
- Block legacy authentication.
- Restrict logon by geographic region.
- Enforce multifactor authentication for all users.
- Enforce compliant devices.
Employee Training
- Conduct regular cybersecurity training sessions for employees to educate them about the dangers of social engineering campaigns. Teach them how to identify suspicious calls and encourage a culture of reporting potential “vishing” attempts to the IT or security team.
How Avertium is Protecting Our Customers
- Fusion MXDR for Microsoft combines Avertium's Fusion MXDR approach with Microsoft Security Solutions, creating the first MDR offering that integrates all aspects of security operations into an active and threat-informed XDR solution. Leveraging Microsoft's comprehensive and cost-effective technology, Fusion MXDR for Microsoft delivers a release of cyber energy, encompassing implementation, optimization, ongoing management, and tuning.
- Avertium simplifies Governance, Risk, and Compliance (GRC) by providing contextual understanding instead of unnecessary complexity. With our cross-data, cross-industry, and cross-functional expertise, we enable you to meet regulatory requirements and demonstrate a robust security posture without any vulnerabilities. Our GRC services include:
- Cyber Maturity
- Compliance Assessments and Consulting
- Managed GRC
- Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A Security Information and Event Management (SIEM) system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior.
MITRE MAP(s)
Scattered Spider
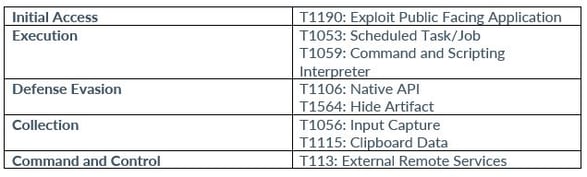
BlackCat (ALPHV)
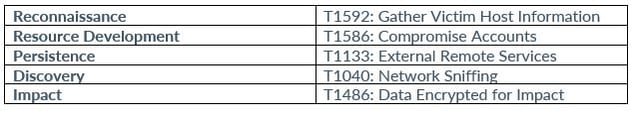
INDICATORS OF COMPROMISE (IOCs)
Scattered Spider
IPV4
- 159[.]223[.]213[.]174
- 169[.]150[.]203[.]51
- 37[.]19[.]200[.]142
- 37[.]19[.]200[.]155
- 45[.]132[.]227[.]213
- 144[.]76[.]136[.]153
- 119[.]93[.]5[.]239
- 146[.]70[.]103[.]228
- 185[.]195[.]19[.]206
- 198[.]54[.]133[.]45
- 217[.]138[.]198[.]196
- 217[.]138[.]222[.]94
- 37[.]19[.]200[.]151
- 45[.]134[.]140[.]177
- 45[.]86[.]200[.]81
- 45[.]91[.]21[.]61
- 89[.]46[.]114[.]66
MD5
- 1e5ad5c2ffffac9d3ab7d179566a7844
- 56fd7145224989b92494a32e8fc6f6b6
- 6639433341fd787762826b2f5a9cb202
- 828699b4133acb69d34216dcd0a8376e
SHA1
- 0272b018518fef86767b01a73213716708acbb80
- 10b9da621a7f38a02fea26256db60364d600df85
- d8cb0d5bbeb20e08df8d2e75d7f4e326961f1bf5
- ec37d483c3c880fadc8d048c05777a91654e41d3
SHA256
- 4188736108d2b73b57f63c0b327fb5119f82e94ff2d6cd51e9ad92093023ec93
- 443dc750c35afc136bfea6db9b5ccbdb6adb63d3585533c0cf55271eddf29f58
- 982dda5eec52dd54ff6b0b04fd9ba8f4c566534b78f6a46dada624af0316044e
- acadf15ec363fe3cc373091cbe879e64f935139363a8e8df18fd9e59317cc918
- cce5e2ccb9836e780c6aa075ef8c0aeb8fec61f21bbef9e01bdee025d2892005
Other IoCs
- Other Scattered Spider IoCs can be found here.
BlackCat (ALPHV)
MD5
- 29efd64dd3c7fe1e2b022b7ad73a1ba5
- 3c5a420aed54867a0fd0d373637595d2
- 44eee3d7f6d60f3390c68ad3f1cb1b77
- 4b940893856bbde6c7c587d7e10ec4d1
- 4bfe8fafe03fe781f75c375bdade54f7
- 60cf9dfc495e4bd99e31b2b6079f654e
- 61b13d54c8dda98b7aa13e75abfdbd12
- 7f4c0d171e104eea3c48e03ade1ec68a
- 825e125eb34abb8197178ed10d5452d5
- adc52a4c68173dce2733dbfe45c5ebe9
- bbeb9589a0f406d0d4921df68641ccf1
- cc51281a38bdc87a7ad0e4b612181ced
- d2848456bc6fc3bdccf6998befeced4b
SHA1
- 1c939f39a93aa425f857f76a8072ef0e43153ed0
- 48579f02785e022db5d31c229be8b9a098134d95
- 6f464abe5f9591b3786f21ef911fc6cd1f717131
- 9d966e90c1c6bc7100e9b089fe6c8ce52a6b379c
- a9ed0ca8e08cf1e7569fcda769351850c748d681
- b2cfe7344875528ce6bf64719c7eadadffb3e567
- b6da15fb313b3c7d66923f6144bac69aa19e74d1
- bd53bd285071966d8799e5d9ceaa84a0b058a4fb
- c219e7bee1cb92e2026a81ac333cd6f439a077b2
- d278d06db4e1b8a6379308a797c0304676a30e10
- d34043b44a7405e1359ef5f4dbebd09f324d9645
- e3b6ea8c46fa831cec6f235a5cf48b38a4ae8d69
- eb410e312adadda3a3d13c608b8bb5ef7ecb812c
SHA256
- 140bcad5397858a7fa35a79dba4cd83decd4ae2927a22983218b3a0efebd8b9e
- 1c2fbab9c849db1e8d8f26d217a7434aad3cab45b6f3c6c2de81b548220779fd
- 20529bcdc538cc28303300bab95b9daeb07264cf7ccdef837f87e26ea2a4f23f
- 234f8d70d92dde7d8f5edee2d3b3152214ef0b86c8e7c30274371fa9880243e6
- 243e1d202848ae99d8ee7a13f08316a8f0d37db93379df2fcbae7ff82754d89e
- 25e6fef0dce4e0f6260442b164ce7305561223429771b96f7448db8f337955cb
- 61c0810a23580cf492a6ba4f7654566108331e7a4134c968c2d6a05261b2d8a1
- 84d33d77ea225839f0f2e473e20108e77f8a3e2a125eac844dc85116ef9792f5
- 85ba48604d680d2786f485d70a6892dcf059c646e28b0a9befe530f9e3e459a5
- b6bb576e3dd58f09218cf455d94e4db253af5f244f70f88abd78af0dc29c1246
- bfa3cf521eefaaecc5d54028b3c12ea571033d4fe98e94d0031912b55071357b
- c97641412ba384933dae4d4de377bc57bd0c9cd6d17b52a9a38c7c9a6eadd64c
- da8c1976b9756cfb9afdcb4eaca193f411f96cee65835a87b3efb3423b33810b
- df1f54952d918b1ddabf543ac50c2dafbca7aad2e5681824c0d1a44416da9c1d
- e616846973de11765207dddbdf7712a74b2d804a08b65badb47f9ef09a640d4f
- e7e8a15588225ae93f2ebc91769352de0d48bfdcfcb93718e66119eb23dee976
- f51166cf076d96c47b5c2ba22e65903b21e4d6735e585e1c51f796108a0a54f9
Other BlackCat IoCs
- Other BlackCat IoCs can be found here.
Supporting Documentation
MGM to lose up to $8.4 million each day as it resolves cyberattack | Fox Business
MGM Resorts Hackers Broke in After Tricking IT Service Desk - Bloomberg
MGM casino's ESXi servers allegedly encrypted in ransomware attack (bleepingcomputer.com)
'Scattered Spider' Behind MGM Cyberattack, Targets Casinos (darkreading.com)
MGM cyber attack: How a phone call may have led to the ongoing hack - Vox
SCATTERED SPIDER Attempts to Avoid Detection with Bring-Your-Own-Driver Tactic (crowdstrike.com)
MGM Resorts breached by 'Scattered Spider' hackers: sources | Reuters
MGM, Caesars File SEC Disclosures on Cybersecurity Incidents (darkreading.com)
Dissecting Scattered Spider: MGM hack fuels more speculation, need for explanation (8newsnow.com)
How the SEC's Proposed Security Rules Could Impact Businesses (avertium.com)
Report: Ransomware group taking credit for MGM cybersecurity issue (ktnv.com)
Casino Giant Caesars Pays $15 Million Ransom to Cyber-Hackers After Breach | National Review
BlackCat/ALPHV reportedly encrypted more than 100 MGM ESXi hypervisors | SC Media (scmagazine.com)
MGM Grand Cyberattack Allegedly Caused by 10-Minute Phone Call (gizmodo.com)
MGM cyberattack continues to create chaos for Vegas operations; SEC notified | Fox Business
A Casino Hack on MGM Resorts Throttles the Betting World - Bloomberg
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.