An In-Depth Look at Chinese APT ToddyCat
Executive Summary
Discovered in December 2020, APT ToddyCat has targeted high-profile victims within the military and government sectors. Their targets include organizations in Vietnam, Taiwan, India, the U.K., Russia, and Iran. Although ToddyCat is a relatively new APT, the threat actor has been responsible for several attacks since their emergence.
ToddyCat is known for exploiting Microsoft Exchange server flaws, including ProxyLogon. The group’s goal appears to be related to geopolitical interests and they have conducted several campaigns. Let’s take a look at ToddyCat’s techniques and tactics, and why it’s important to implement cyber security best practices to prevent an attack from APTs like ToddyCat.

toddycat
As we stated previously, ToddyCat is a new APT that is unrelated to other known actors. The group has been active since December 2020 and has attacked several high-profile organizations within the government and military sectors. During that time, ToddyCat started its campaign off by compromising Microsoft Exchange Servers in Taiwan and Vietnam by using an unknown exploit.
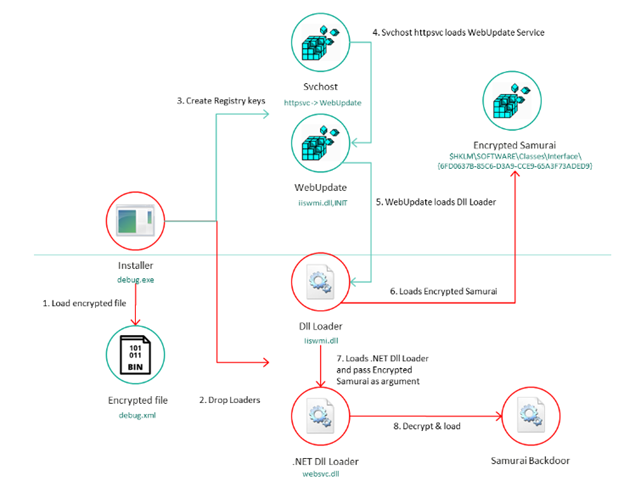
The unknown exploit led to the creation of the web shell, China Chopper. The web shell was used to initiate a multistage infection chain, which included custom loaders used to stage a passive backdoor called Samurai. Between December 2020 and February 2021, ToddyCat was observed targeting three organizations in Taiwan and Vietnam.
It wasn’t until February 26, 2022, into early March 2022, that the APT escalated their attacks and began abusing ProxyLogon to compromise several unnamed organizations across Europe and Asia. ToddyCat was able to scan for and target unpatched Microsoft Exchange servers across the two continents. It is suspected that ToddyCat abused the ProxyLogon vulnerability in December 2020, which allowed them to gain remote code execution on vulnerable servers to deploy China Chopper webshells.
tactics + techniques
In March 2021, ESET Research published a report detailing the attack of exchange servers from at least ten APT groups. At the time ToddyCat was still unnamed, but the group was one of the APT’s targeting the servers and exploiting Microsoft Exchange vulnerabilities. Other threat actors (also APTs) included LuckyMouse, Tick, Winnti Group, and Calypso.
The Microsoft Exchange vulnerabilities were discovered by security researcher, Orange Tsai, and the cluster of activity observed by ESET Research was named Websiic. The researchers observed the cluster targeting seven email servers that belonged to private companies – with domains in the IT, engineering, and telecommunications sectors. ESET Research suspected that the operators behind the cluster had access to the Microsoft exchange vulnerabilities before a patch was released.
Websiic was identified due to the presence of a loader as its first staged named google.log or google.aspx, and an encrypted configuration file, named access.log. According to ESET Research, the loader stops a service that is identified in the config and creates a new entry under the Windows registry. After the loader was deployed on the victims from Websiic, the second stage loader was observed on one of the victim’s computers. As a result, seven victims were flagged by the presence of the first loader.
Image 1: ToddyCat's Infection Window
Source: SecureList
Samurai
Samurai is the final stage of ToddyCat’s infection chain and was used during the second wave of Microsoft Exchange server attacks – targeting Iran, Russia, the U.K., and India. Samurai is a passive backdoor that usually works on ports 80 and 443. The backdoor allows arbitrary C# code execution and is used with modules that allow ToddyCat operators to control the remote system and move laterally inside a network.
In some cases, Samurai was observed being used to launch another malicious program called Ninja. Ninja is more than likely a component of an unknown-post exploitation toolkit that’s exclusive to ToddyCat. A collaborative tool, Ninja allows several operators to work on the same machine at the same time. Ninja allows ToddyCat to control remote systems, avoid detection, and penetrate a targeted network via a large set of commands.
The next wave of attacks from ToddyCat began May 2021 and lasted until February 2022. The APT targeted the same cluster of countries named during the first wave of attacks, but also included organizations from Uzbekistan, Kyrgyzstan, and Indonesia. During this phase, ToddyCat expanded even more and included desktop systems in addition to Microsoft Exchange servers.
ToddyCat favors attacking high-profile organizations within the military and government, including military contractors. The victims seem to be linked to industry sectors and countries that have been targeted by Chinese speaking groups.
apts are persistent
As of late, there has been an uptick in APT activity, and they are becoming more visible as the weeks progress. Since the war between Russia and Ukraine began, APTs like Muddy Water, Aoqin Dragon, Bronze Mohawk, Bronze Starlight, and ToddyCat have taken advantage of the fact that most cyber security researchers and analysts have their attention on the Russia Ukraine cyber war.
Unlike data extortion groups and ransomware groups, APTs like ToddyCat are not after money. Their purpose is to glean classified data, trade secrets, and other forms of intellectual property that can be used politically. At the moment, there are no reports of ToddyCat demanding ransoms from their targets. Just like other politically motivated groups, ToddyCat targets large and high-value organizations within a small community – military and government.
However, some APTs are starting to use ransomware to disguise their cyberespionage activities. Bronze Starlight is a China linked state-sponsored APT that uses HUI Loader to drop ransomware like Rook and LockFile. Bronze Riverside is another APT that uses HUI Loader to drop ransomware. The goal of these APTs is to distract incident responders by deploying the ransomware and to destroy evidence of an intrusion.
According to SecureWorks, Bronze Starlight is only interested in cyberespionage due to their operational cadence and victimology not aligning with financially motivated cyber crime operations. Their ransomware targets a small number of victims over a short period of time and then ceases operations permanently – an operational cadence that is not indicative of a financially motivated group.
APTS like Bronze Starlight and ToddyCat are persistent and will stay in their victim’s networks and systems for months or years before they are discovered. ToddyCat uses several techniques to avoid detection and keep a low profile, making it extremely difficult for them to be detected by analysts. Unfortunately, by the time they are discovered it’s too late and they’ve already taken the information they were after.
cyber security best practice - patching
One of the ways ToddyCat was able to infiltrate their victim’s networks and systems was through unpatched Microsoft Exchange servers. Patching is a cyber security best practice that gets overlooked but is just as important as having the latest advanced threat hunting tools. When cyber security professionals talk about patching devices, they are simply saying that you need to apply updates to your software as those updates become available.
Common areas that will need patches include operating systems, applications, and embedded systems (like network equipment). When a bug is found after the release of a piece of software, a patch can be used to remediate it. Patching helps ensure that assets in your environment are not vulnerable to attackers.
In 2017, Equifax suffered a data breach that affected over 145 million people. It was one of the largest breaches of its kind in history and was the result of an employee who didn’t apply the most recent patch for Apache Struts. The patch was available for two months before the company was breached.
Another example of how important it is to patch is the Log4Shell exploit. In January 2022, Avertium’s Cyber Threat Intelligence team published a Threat Intelligence Report detailing the Log4Shell (CVE-2021-44228). Log4Shell was a zero-day critical vulnerability found in the Apache Log4j2 Java-base logging library. The flaw was an unauthenticated remote code execution vulnerability that allowed for complete system takeover. Attackers had the ability to install cryptominers, steal data, and steal credentials.
Major enterprises like Amazon, Apple, and Tesla were all affected by Log4Shell, and cyber security professionals were in a hurry to come up with a solution to this massive problem. The situation quickly went from bad to worse when it was discovered that the first patch Apache issued for CVE-2021-44228 didn’t exactly fix the problem.
After the news broke about how easy it was to exploit Log4j2, threat actors made swift moves. Log4Shell resulted in massive world-wide scanning with the payloads running from miners, Unix DDoS malware, and framework stagers pushed to compromised hosts. Several threat actors took advantage of the Log4Shell exploit, with one of those threat actors being Conti.
Additionally, The Iranian threat actor, DEV-0270, and Chinese APT, APT10, were among the first to aggressively exploit Log4Shell. Mandiant observed reconnaissance activity linked to APT10 and DEV-0270 successfully attacked multiple U.S. companies via ransomware deployments.
One would think that because Log4Shell was so dangerous and easy to exploit, that organizations would rush to patch their devices. However, in March 2022 researchers at Qualys’s found that more than 150 million IT assets across the world had vulnerable application installations of Log4j, with 80% of them being open-source applications. Of those application installations, 30% of Log4j instances were vulnerable to exploitation and only 70% of the Apache Log4j applications had been patched. Developers were still downloading vulnerable versions of Log4j. Not patching and downloading vulnerable versions of software was how threat actors were still able to exploit Log4Shell.
Because leaving devices unpatched leads to cyber attacks, the FTC issued a strong warning to organizations who don’t patch their devices. The warning stated that the FTC will use its full legal authority and pursue companies who fail to patch vulnerable devices. Data breaches, financial loss, and other irreversible damage can happen as the result of not patching. Organizations should not wait until the eleventh hour to patch devices when so many people rely on them to keep their information safe.
How Avertium is Protecting Our CUSTOMERS
Once an APT like ToddyCat is inside a network, it can give them unlimited access to do further reconnaissance. Chinese APTs are some of the world’s oldest and most skilled when it comes to cyber espionage. Avertium is here to keep your organization safe and to mitigate any attacks caused by Chinese APTs like ToddyCat:
- To identify the source of your breach and the scope that it reached; you’ll want to include Avertium’s DFIR (Digital Forensics and Incident Response) services in your protection plan. We offer DFIR to mitigate damage from a successful breach. This service is provided as an on-demand crisis response service, as well as retainer-based program.
- MDR provides an in-depth investigation into potential threats on an organization’s network. Avertium’s risk-based approach to managed security delivers the right combination of technology, field-validated threat intelligence, and resource empowerment to reduce complexity, streamline operations, and enhance cybersecurity resilience. If you need a more advanced security solution, MDR is the next step. MDR is an outsourced security control solution that includes the elements of EDR, enhanced with a range of fundamental security processes.
- Avertium offers VMaaS to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Fusion MXDR is the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is great than the sum of its parts.
- Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
Avertium’s Recommendations
- According to SecureList, Samurai’s backdoor cannot be detected by watching the open TCP ports due to it using .NET HTTPListener class, which is built on top of HTTP.sys and allows for different processes to share the same ports. To check to see if the backdoor is running, execute the following command: #>netsh http show servicestate verbose=yes
- Cybersecurity Education: Educate your employees on cyber security preparedness and the dangers of opening potentially malicious documents. Annual or quarterly training modules can help prevent threat actors from tricking employees into opening malicious email attachments.
- Monitor users' web browsing habits; restrict access to sites with unfavorable content.
- Exercise caution when opening e-mail attachments even if the attachment is expected and the sender appears to be known.
- Risk Analysis: Prevent an attack by ensuring your organization has a detailed defense strategy based on a risk analysis approach.
- Maintain up-to-date antivirus signatures and engines.
- Enable a personal firewall on agency workstations, configured to deny unsolicited connection requests.
- Keep operating system patches up to date.
- Tabletop Exercises: Have a good cyber incident response plan in place that has been tested with tabletop exercises.
- Security Review: Be sure to review your cyber incident response plan and improve it every time it’s tested on real cyber threats
- Maintain situational awareness of the latest threats and implement appropriate Access Control Lists (ACLs).
- Scan for and remove suspicious e-mail attachments; ensure the scanned attachment is its "true file type" (i.e., the extension matches the file header).
- Disable File and Printer sharing services. If these services are required, use strong passwords or Active Directory authentication.
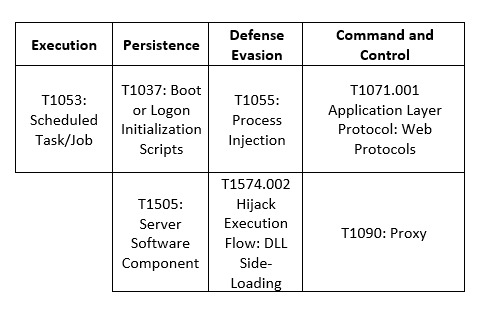
MITRE Map
Indicators of Compromise (IoCs)
Registry Keys
- $HKLM\System\ControlSet\Services\WebUpdate
- $HKLM\System\ControlSet\Services\PowerService
- $HKLM\SOFTWARE\Classes\Interface\{6FD0637B-85C6-D3A9-CCE9-65A3F73ADED9}
- $HKLM\SOFTWARE\Classes\Interface\{AFDB6869-CAFA-25D2-C0E0-09B80690F21D}
File Paths
- C:\inetpub\temp\debug[.exe]
- C:\Windows\Temp\debug[.exe]
- C:\Windows\Temp\debug[.xml]
- C:\Windows\Microsoft.NET\Framework64\v2.0.50727\Temporary ASP.NET Files\web[.exe]
- C:\Users\Public\Downloads\dw[.exe]
- C:\Users\Public\Downloads\chrome[.log]
- C:\Windows\System32\chr[.exe]
- C:\googleup[.exe]
- C:\Program Files\microsoft\exchange server\v15\frontend\httpproxy\owa\auth\googleup[.log]
- C:\google.exe
- C:\Users\Public\Downloads\x64[.exe[
- C:\Users\Public\Downloads\1[.dll]
- C:\Program Files\Common Files\microsoft shared\WMI\iiswmi[.dll]
- C:\Program Files\Common Files\microsoft shared\Triedit\Triedit[.dll]
- C:\Program Files\Common Files\System\websvc[.dll]
- C:\Windows\Microsoft.NET\Framework\sbs_clrhost[.dll]
- C:\Windows\Microsoft.NET\Framework\sbs_clrhost[.dat]
- C:\Windows\Microsoft.NET\Framework64\v2.0.50727\Temporary ASP.NET Files\web[.xml]
- C:\Users\Public\Downloads\debug[.xml]
- C:\Users\Public\Downloads\cache[.dat]
- C:\Windows\System32\config\index[.dat]
- C:\Windows\Microsoft.NET\Framework\netfx[.dat]
- %ProgramData%\adobe\2[.dll]
- %ProgramData%\adobe\acrobat[.exe]
- %ProgramData%\git\git[.exe]
- %ProgramData%\intel\mstacx[.dll]
- %ProgramData%\microsoft\drm\svchost[.dll]
- %ProgramData%\microsoft\mf\svchost[.dll]
- %ProgramData%\microsoft\mf\svhost[.dll]
- %program files%\Common Files\services\System.Core[.dll]
- %public%\Downloads\1[.dll]
- %public%\Downloads\config[.dll]
- %system%\Triedit.[dll]
- %userprofile%\Downloads\Telegram Desktop\03.09.2021 г[.zip]
- %userprofile%\Downloads\Telegram Desktop\Тех.Инструкции.zip
- %userprofile%\libraries\1[.dll]
- %userprofile%\libraries\chrome[.exe]
- %userprofile%\libraries\chrome[.log]
- %userprofile%\libraries\config[.dll]
- C:\intel\2[.dll]
- C:\intel\86[.dll]
- C:\intel\x86[.dll]
Hashes
- 5cfdb7340316abc5586448842c52aabc
- 93c186c33e4bbe2abdcc6dfea86fbbff
- 5a912beec77d465fc2a27f0ce9b4052b
- f595edf293af9b5b83c5ffc2e4c0f14b
- 5a531f237b8723396bcfd7c24885177f
- 1ad6dccb520893b3831a9cfe94786b82
- f595edf293af9b5b83c5ffc2e4c0f14b
- 8a00d23192c4441c3ee3e56acebf64b0 (Samurai)
- 5e721804f556e20bf9ddeec41ccf915d (Ninja Trojan)
- 33694faf25f95b4c7e81d52d82e27e7b
- 832bb747262fed7bd45d88f28775bca6
- 8fb70ba9b7e5038710b258976ea97c98
- ee881e0e8b496bb62ed0b699f63ce7a6
- ae5d2cef136ac1994b63c7f8d95c9c84
- 5c3bf5d7c3a113ee495e967f236ab614
- bde2073dea3a0f447eeb072c7e568ee7
- 350313b5e1683429c9ffcbc0f7aebf3b
Supporting Documentation
ToddyCat: an advanced threat actor targets high-profile entities with new malware (zawya.com)
Kaspersky unveils unknown APT actor 'ToddyCat' (techtarget.com)
Exchange servers under siege from at least 10 APT groups | WeLiveSecurity
Microsoft Exchange servers hacked by new ToddyCat APT gang (bleepingcomputer.com)
ToddyCat APT Hacks Microsoft Exchange Servers | Cyware Alerts - Hacker News
Understanding Cybersecurity Best Practices (avertium.com)
An In-Depth Look at Chinese APT, Aoqin Dragon (avertium.com)
"Bronze Mohawk" & Cyber Espionage (avertium.com)
New ToddyCat APT targets high-profile entities in Europe and AsiaSecurity Affairs
(1) New Messages! (secureworks.com)
ToddyCat claws at Asian governments - Security Boulevard
Chinese APT 'Bronze Starlight' Uses Ransomware to Disguise Cyberespionage | SecurityWeek.Com
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.
Related Resource: An In-Depth Look at Chinese APT, Aoqin Dragon