The Top 5 Cyber Threats in the Energy Sector
Executive Summary
In the past few years, the energy sector has seen numerous cyber attacks that could have been avoided had the proper security measures been in place. One of the most popular energy attacks is the attack on Colonial Pipeline. In May 2021, the threat actor, DarkSide, launched a ransomware supply-chain attack that would end up becoming one of the largest in U.S. history.
The threat actor gained access to Colonial Pipeline’s virtual private network (VPN) account due to a single compromised password. The account that was compromised allowed employees to remotely access the company’s computer network. At the time of the attack, the account wasn’t in use but could still be used to access the fuel company’s network. The energy company ended up paying DarkSide $4.4 million in ransom.
If Colonial Pipeline practiced cyber security best practices by taking inventory of dormant VPN accounts and using multi-factor authentication, their breach could have been avoided. Threat actors want to maximize their profits and will go after critical services if it means a big pay day.
However, without the services that our daily lives depend on, the wellbeing of millions of people is threatened.
Unfortunately, the technology within the energy sector is outdated because it was not built with digital transformation in mind. Therefore, legacy equipment often cannot be patched or upgraded. It’s important for organizations within the sector to consistently implement cyber security best practices to keep their operations running efficiently. Let’s take a look at the top five cyber threats within the energy sector and why energy organizations need cyber security best practices to keep their cyber environments safe.
1) Supply chain attacks
A supply chain attack happens when threat actors access an organization’s network via a third-party vendor or supplier. Access can be gained through viruses or malicious software, giving the attacker keys to sensitive information, customer records, and payment information. Because a supply chain can be large in scope, the attack itself can be difficult to trace.
As previously stated, the attack on Colonial Pipeline was one of the largest supply-chain attacks in U.S. history. A virtual private network (VPN) account was compromised because the organization didn’t take inventory of dormant VPN accounts, and there was no multifactor authentication for the account user.
After the ransomware attack, researchers discovered that the password for the account was inside a batch of leaked passwords on the dark web. It’s suspected that the Colonial Pipeline employee probably re-used that password on another previously hacked account. Currently, it is not known how DarkSide obtained the correct username and password.
As a result of the attack, Colonial Pipeline had to shut down the fuel pipeline, leaving gas stations, businesses, and households without fuel. Additionally, the news of a cyber attack made its rounds and people started panic buying which resulted in gas shortages along the east coast. DarkSide stole about 100 gigabytes of data from the company and threatened to leak it if they refused to pay a ransom.
In March 2022, the United States Department of Justice unsealed indictments detailing alleged Russian government hackers’ efforts to compromise and control critical infrastructure across the globe via supply chain attacks. One of those attacks was to include at least one nuclear power plant. The campaign was allegedly spearheaded by three officers from Russia’s Federal Security Service (FSB).
From 2012 to 2014, the officers worked on a project named “Dragonfly.” The project involved a supply chain attack that targeted updates of industrial control systems and supervisory control and data acquisition systems (ICS and SCADA). This resulted in legitimate updates to the software being infected with Havex (malware). The malware allowed the threat actors to create backdoors and scan networks for additional targets. Seventeen thousand devices were infected in the U.S. and poisoning the SCADA apps could have disrupted the U.S. power supply and even nuclear plants.
2) Incomplete integration of systems
Incomplete integration of systems is a major challenge for the energy sector. Typically, an energy organization’s cyber threat landscape includes OT (Operational Technology) and IT (Information Technology) architectures, a mixture of legacy and modern technology, and systems that were acquired during mergers or acquisitions. In order to integrate the right tools into control, transmission, generations, distribution, and field networks while remaining compliant, energy organizations will need to have custom solutions with open standards and APIs to help with streamlining.
If there is a mixture of legacy and modern equipment, it means that some systems won’t be able to be patched or hardened. Legacy equipment is one of the main challenges of the energy sector. OT networks are usually built on equipment that is over 15 years old, and those old networks are becoming more connected. Due to the convergence of IT and OT environments there are challenges with security.
Operational Technology networks that were in place 15 to 20 years ago were not originally built for internet connectivity. While IT technologies can be patched and updated as needed, OT networks often cannot be shut down. This leaves the systems sitting on networks for months to years waiting for maintenance downtime so security updates can be made. Most large OT environments will have scheduled downtime at least once per year. The systems generally cost millions of dollars if they don’t take downtime and reliability seriously. In some cases, it has been the general IT staff that do not take security of corporate systems as seriously as they should. The lack of totality leads to breaches, and this is what took place in the case of Colonial Pipeline.
In March 2019, a cyber attack impacted a U.S. power grid organization. For ten hours, attackers repeatedly caused firewalls to reboot. Although the attack didn’t cause a disruption in the electric power supply, the incident occurred due to a known firewall vulnerability that went unpatched. After investigating, a power grid operator stated that they failed to apply firmware updates to the firewalls that were compromised.
According to the grid operator, the entity lacked a proper firmware review process to vet security updates before being deployed. While they were actively trying to standardize the process, the procedure was not ready in time – resulting in a holdup of firmware updates that had not been reviewed or deployed. The incident left security holes open on the company’s network.
3) Ransomware & Incident Response
The energy sector faces great risk of ransomware attacks by ransomware gangs and nation-state threat actors. Not only can a ransomware attack disrupt the operation of an energy organization, but it can also be costly to remediate. A ransomware attack on an energy provider’s systems could be catastrophic for populations. Likewise, not having an incident response plan in place could be damaging to the organization’s reputation.
In August 2022, the ransomware gang Ragnar Locker claimed responsibility for attacking Greece’s largest natural gas supplier, DESFA. The attack impacted the availability of some of DESFA’s systems, and the attackers allegedly stole and published over 360 GB of data. Ragnar Locker has been on the Federal Bureau of Investigation’s (FBI) radar since the gang breached over fifty organizations within ten critical infrastructure sectors.
Ragnar Locker is known for using the double extortion tactic, which involves threat actors exfiltrating sensitive data, then triggering the encryption attack, and ultimately threatening to leak the data if the demanded ransom isn’t paid. To avoid prevention and detection, the threat actor frequently changes their obfuscation techniques.
Ragnar Locker deletes shadow copies and disables antivirus countermeasures, followed by using a PowerShell script to move from one company network to another. Before the ransomware is deployed, Ragnar Locker steals files and uploads them to servers before publishing them – this is done just in case their victim refuses to pay the demanded ransom. Obfuscation techniques protect the ransomware code, and those techniques include adding junk code in addition to encryption.
Ragnar Locker’s attack on DESFA makes this the second time a large pipeline company has been hit by ransomware in recent years. The increase in ransomware attacks across the energy sector prompted the U.S., the UK, and the Australian authorities to issue a joint warning regarding ransomware attacks on critical infrastructure. In 2021, 14 out of 16 U.S. critical infrastructure sectors were hit by ransomware.
4) Identity & access management (iam) inefficiencies
As the energy sector tries to upgrade older and outdated infrastructure to take advantage of emerging technologies, identity and access management has become an issue. The new technology, devices, and systems connected to utilities’ grid networks needs protection from threat actors.
Controlling access to networked resources such as information technology, equipment, ICS, and networked resources is crucial. Often, IAM systems exist in silos, and their employees who manage them lack ways to coordinate access to devices and facilities in those silos. Lack of IAM systems results in inefficiency and security risks.
For example, there is an engineer in New Hampshire who has access to several remote terminal units connected to the company’s network. She then gets a new opportunity in California and quits her job. However, once she leaves, the energy company she worked for realizes there is no centralized IAM system in place to manage her access to various facilities and systems - making it cumbersome and time consuming to try and manage her access. To help prevent this scenario from occurring, IAM best practices would ensure the right person/entities would have the appropriate level of access for the right resources.
Not only will proper IAM processes keep cyber environments safe, but these processes will also help energy organizations build toward a Zero Trust model and will help secure both traditional networks and cloud-based architectures. Due to retirements, promotions, and resignations, some energy organizations have shifted the responsibility of IAM away from IT departments to human resources. Human resources has a better overview of employee information, and giving them authority over IAM ensures quick adjustments, thus closing vulnerabilities.
5) mobile device phishing
Mobile phishing attacks are probably the last thing you expected to make this list, yet mobile phishing attacks targeting employees in the energy sector rose by 161% during the second half of 2020 and the first half of 2021. Outdated and vulnerable devices are an issue for all sectors, but the energy sector is the most targeted.
According to a report published by Lookout, there was a 44% increase in mobile phone devices connecting to energy organizations over the course of 12 months between 2020 and 2021. In the sector, partners and employees are using mobile devices to connect to OT, sensitive information, and industrial control systems. Although the mobile devices increase productivity, they contain a lot of personal and work apps leaving the devices extremely vulnerable to cyber attacks.
Since the COVID-19 pandemic, many people work from home and use personal mobile devices or tablets. The employees use VPNs (Virtual Private Networks) to access their corporate networks making them easy targets for attackers who use phishing techniques to steal VPN credentials. The attacks involve the threat actor employing SMS, email, login pages, and phishing apps on fake corporate websites. The credentials they steal help them gain access to an organization’s internal network which in turn can be used for lateral movement.
Once the threat actor is in the network, they can locate vulnerable systems and launch attacks against flawed industrial control systems. Attackers know that industrial control systems can carry unidentified flaws for several years before they are noticed and fixed. Lookout’s report stated that unmanaged mobile devices in the industry increased 41% in 2021, meaning organizations are losing control and visibility over how the mobile devices are used.
Lookout’s report also stated that 56% of Android users in the energy sector were exposed to vulnerabilities due to running out-of-date versions of Android’s operating system. iOS users were much less affected, benefiting from automated software updates by default. Securing mobile endpoints that employees use can keep phishing attacks and mobile app threats at bay.
In February 2021, Npower, a gas and electricity company, had to permanently withdraw its mobile app after threat actors used it to access their customers’ personal information (last four digits of bank accounts and sort codes). The attackers accessed the customer accounts using login data from another website, leaving customers open to fraud.
recent attacks on energy
Lazarus
In August 2022, North Korean APT group Lazarus (APT38) began attacking the energy sector by exploiting VMWare Horizon servers to access the networks of energy providers in Japan, the U.S, and Canada. The group is known for cyber espionage and has been responsible for hundreds of sophisticated cyber attacks.
Lazarus is a state-backed threat actor and was recently seen using phishing emails to trick deBridge Finance employees into launching malware that collects information from Windows systems and allows the delivery of additional malicious code. Between February and January 2022, the group targeted energy organizations by leveraging the VMWare Horizon vulnerabilities for initial access. After gaining access, the group uses a custom malware family like “YamaBot” and “VSingle”, and “MagicRAT” to search for a steal data from devices.
In April 2022, Lazarus used social engineering to trick victims into downloading Trojanized cryptocurrency applications on Windows or macOS operating systems. According to CISA, Lazarus used the applications to gain access to their victims’ computer, propagate malware across their network, and steal private keys – activities that enabled follow-on activities that initiate fraudulent blockchain transactions. The group has also been associated with other North Korean threat actors that have been extremely visible lately (NOBELIUM, H0ly Gh0st, and Kimsuky).
BlackCat
In addition to Lazarus, the ransomware gang BlackCat (ALPHV) recently took responsibility for an attack on Italy’s energy agency “Gestore dei Servizi Energetici SpA” (GSE). The company promotes and supports renewable energy sources across Italy. The attack took place at the beginning of September 2022, forcing GSE to shut down their systems and website to stop the attackers from gaining access to data.
BlackCat stole 700 GB worth of data from GSE, and the threat actors claim the data is sensitive (contracts, reports, project information, and accounting documents). The attack came on the heels of another security incident involving Eni SpA – the largest energy company in Italy.
Additionally, in July 2022, BlackCat attacked a natural gas pipeline and electricity network operator in central Europe called Creos Luxembourg S.A.
Active since at least November 2021, BlackCat is a RaaS (Ransomware-as-a-Service) gang whose ransomware is written in the Rust programming language. The ransomware programming language is compiled for both Windows and Linux. The sample below is one of several BlackCat executables compiled in early November 2021.
Image 1: BlackCat Executable
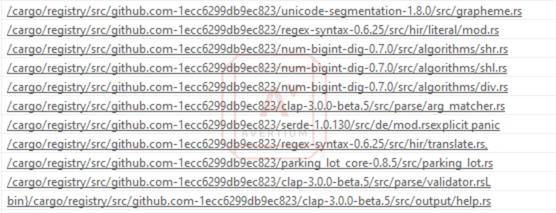
Source: Avertium's Cyber Threat Intelligence Team
In the above image, we see not only the key work cargo, but also “.rs” file extensions being referenced. Cargo is the built-in package manager for Rust, and “.rs” is the file extension used for rust packages and source code. Unfortunately, the most useful strings, that refences IP addresses or file content and commands, are encrypted or obfuscated, and are not easily parsed out. However, we can still see some of the API calls this program makes, which gives some hints about the functionality of the program.
Image 2: BlackCat API Calls
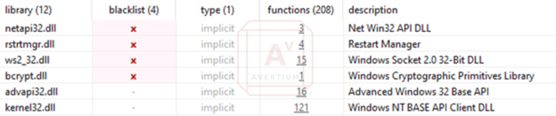
Source: Avertium's Cyber Threat Intelligence Team
During successful execution of the ransomware, a Y: and Z: drive are both added to the host. While nothing is visible to the end user on the Y: drive, the Z: drive contains just one visible file. That file is the ransom note, which informs the victim that information has been stolen, and instructs them on how to start recovery.
Image 3: Ransom Note File
Source: Avertium's Cyber Threat Intelligence Team
Image 4: Ransom Note
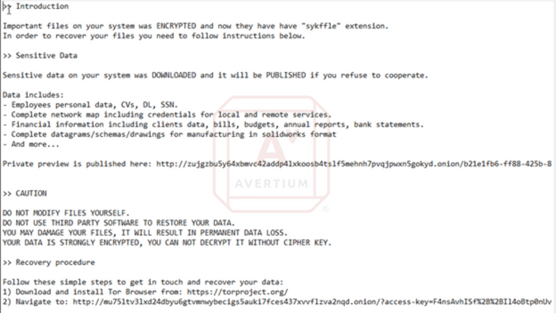
Source: Avertium's Cyber Threat Intelligence Team
how the energy sector can take action
No one can imagine what an entire day would be like without the products and services we use. The energy sector is a critical part of society and connects all critical infrastructure sectors. The U.S. economy cannot function without the energy sector. A cyber attack on energy would mean loss of electricity, gas, and oil, which then disables emergency services and even communication networks. This would leave the U.S. extremely vulnerable without the necessary resources to aid in a time of crisis.
Fortunately, all hope is not lost, and the energy sector can keep cyber threats to a minimum if they implement basic best practices for the sector:
- Ransomware and Incident Response – Your organization should be able to prevent, detect, and respond to attacks. Make sure your organization reviews internal governance processes and creates an incident response plan to help cyber security professionals assess and remediate the breach.
- Supply Chain Attacks – Managing your supply chain risk should be a critical part of an energy company’s risk management strategy. Investing in SOC analysts can ensure that your organization’s cyber security infrastructure is examined and that problems are identified. Password management also keeps supply chain attacks to a minimum.
- Incomplete Integration of Systems – Ensure your energy organization has holistic assessments and strategies that integrate cyber hygiene and compliance. This will provide protection for legacy systems and build organizational resilience.
- IAM Issues – Hybrid IAM solutions in conjunction with best in-class processes and technology in regulation compliant technologies will protect energy infrastructure information and personally identifiable information. This will also bridge the gap between aging OT and IT architectures.
- Mobile Device Phishing Attacks – Educating employees on how to spot phishing attempts is crucial when they are checking email and other communication platforms (phone, messaging, etc.) while using any electronic device connected to the internet, especially mobile devices. Implementing best practices like using MFA, turning on spam filters, and conducting regular tabletop exercises can help prevent phishing attacks via mobile devices.
How Avertium is Protecting Our CUSTOMERS
It’s important to get ahead of the curve by being proactive with protecting your organization, instead of waiting to put out a massive fire. Avertium offers the following services to keep your organization safe:
- Avertium offers user awareness training through KnowBe4. The service also Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
- Avertium offers VMaaS to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap
- Fusion MXDR is the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is great than the sum of its parts.
- Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
- Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A Security Information and Event Management (SIEM) system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior.
- Avertium offers Zero Trust Network as a Service (ZTNaaS) for any organization that wants to control their attack surface. The zero-trust security model delivers exactly what the name promises: it's an IT security concept that specifies no access is allowed until the successful completion of authentication and authorization processes.
Avertium’s Recommendations
To prevent ransomware attacks, phishing attacks , IAM Inefficiencies, supply chain attacks, and attacks via unpatched software, Avertium and the FBI recommend that you do the following:
- Use strong credentials and multi-factor authentication.
- Patch and update your software.
- Educate your employees on cyber security best practices.
- Upgrade your devices when software is obsolete.
- Use hard passwords and enforce this amongst your institution.
- Encrypt your data and always have backups (test your backups often).
- Disable unused remote access/RDP ports and monitor remote access/RDP logs.
- Require administrator credentials to install software.
- Audit user accounts with administrative or elevated privileges and configures access controls with the least privilege in mind.
- Implement network segmentation.
- Monitor IoT devices at all times.
- Gain visibility into how many IoT devices are connected to your network.
- If you don’t have one already, develop a cyber security policy that employees must follow.
- Advise employees not to click on suspicious links or open email attachments from suspicious senders.
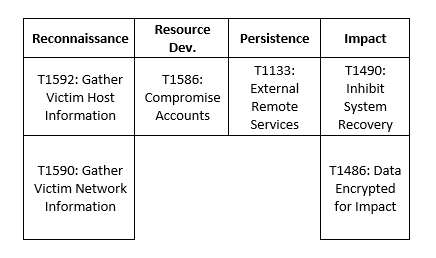
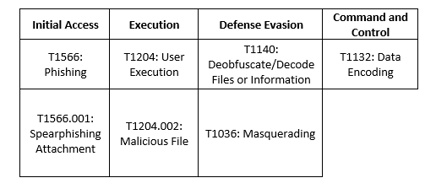
MITRE Map
BlackCat
Lazarus
Indicators of Compromise (IoCs)
Lazarus
- bb266486ee8ac70c0687989e02cefa14
- 11203786b17bb3873d46acae32a898c8dac09850
- 0c6f444c6940a3688ffc6f8b9d5774c032e3551ebbccb64e4280ae7fc1fac479
- 49152:rEqvaaAjc2hdKjb8WXqE1PiEbE/TKMt3/RgaJ2wW4PRT8O1:rbyaALKjwWXV1P9oVvwwW4JT8
- b4c9b903dfd18bd67a3824b0109f955b
- 505262547f8879249794fc31eea41fc6
- 76c3d2092737d964dfd627f1ced0af80
- cb9e18e21226a89ce2c26c695a989e0d
- 61d1a5b8f242706a39d06316e4c66b01141b4ab3
- b312dd587e8725edf782e0c176b902fbbfc01468
- ec062c8c6e77808ee2b3573f91eede294d572509
- bffe910904efd1f69544daa9b72f2a70fb29f73c51070bde4ea563de862ce4b1
- f32f6b229913d68daad937cc72a57aa45291a9d623109ed48938815aa7b6005c
- f78cabf7a0e7ed3ef2d1c976c1486281f56a6503354b87219b466f2f7a0b65c4
- 188.27[.73]
- a3555a77826df6c8b2886cc0f40e7d7a2bd99610
- f6827dc5af661fbb4bf64bc625c78283ef836c6985bb2bfb836bd0c8d5397332
- 4df757390adf71abdd084d3e9718c153
- 70652edadedbacfd30d33a826853467d
- c7c8019f4b5314cd2543ab2ac65d3ea4
- 00331e5f972a98755811c02ec47301336a824a34
- 45ead9fc05f76d0979bd0f5687bfdc0cd42aea20
- 871b08e580e99507501368c967b736e5c1cd38c0
- 196fb1b6eff4e7a049cea323459cfd6c0e3900d8d69e1d80bffbaabd24c06eba
- 1c926fb3bd99f4a586ed476e4683163892f3958581bf8c24235cd2a415513b7f
- 1f8dcfaebbcd7e71c2872e0ba2fc6db81d651cf654a21d33c78eae6662e62392
- 23eff00dde0ee27dabad28c1f4ffb8b09e876f1e1a77c1e6fb735ab517d79b76
- ca932ccaa30955f2fffb1122234fb1524f7de3a8e0044de1ed4fe05cab8702a5
- d20959b615af699d8fff3f0087faade16ed4919355a458a32f5ae61badb5b0ca
- http://64.188.27.73/adm_bord/login_new_check[.php]
- http://64.188.27.73/board/logo_adm_org[.gif]
- http://64.188.27.73/board/mfcom1[.gif]
- http://64.188.27.73/board/pct[.gif]
- http://64.188.27.73/board/tour_upt[.html]
- http://gendoraduragonkgp126.com/board/index[.php]
- gendoraduragonkgp126[.com]
BlackCat
- id7seexjn4bojn5rvo4lwcjgufjz7gkisaidckaux3uvjc7l7xrsiqad[.onion]
- sty5r4hhb5oihbq2mwevrofdiqbgesi66rvxr5sr573xgvtuvr4cs5yd[.onion]
- htnpafzbvddr2llstwbjouupddflqm7y7cr7tcchbeo6rmxpqoxcbqqd[.onion]
- aoczppoxmfqqthtwlwi4fmzlrv6aor3isn6ffaiic55wrfumxslx3vyd[.onion]
- alphvmmm27o3abo3r2mlmjrpdmzle3rykajqc5xsj7j7ejksbpsa36ad[.onion]
- 2cuqgeerjdba2rhdiviezodpu3lc4qz2sjf4qin6f7std2evleqlzjid[.onion]
- zujgzbu5y64xbmvc42addp4lxkoosb4tslf5mehnh7pvqjpwxn5gokyd[.onion]
- mu75ltv3lxd24dbyu6gtvmnwybecigs5auki7fces437xvvflzva2nqd[.onion]
- f815f5d6c85bcbc1ec071dd39532a20f5ce910989552d980d1d4346f57b75f89
- c3e5d4e62ae4eca2bfca22f8f3c8cbec12757f78107e91e85404611548e06e40
- 74464797c5d2df81db2e06f86497b2127fda6766956f1b67b0dcea9570d8b683
- 4e18f9293a6a72d5d42dad179b532407f45663098f959ea552ae43dbb9725cbf
- 1af1ca666e48afc933e2eda0ae1d6e88ebd23d27c54fd1d882161fd8c70b678e
- 15b57c1b68cd6ce3c161042e0f3be9f32d78151fe95461eedc59a79fc222c7ed
- 13828b390d5f58b002e808c2c4f02fdd920e236cc8015480fa33b6c1a9300e31
- c8b3b67ea4d7625f8b37ba59eed5c9406b3ef04b7a19b97e5dd5dab1bd59f283
- bd337d4e83ab1c2cacb43e4569f977d188f1bb7c7a077026304bf186d49d4117
- 7b2449bb8be1b37a9d580c2592a67a759a3116fe640041d0f36dc93ca3db4487
- 38834b796ed025563774167716a477e9217d45e47def20facb027325f2a790d1
- 2cf54942e8cf0ef6296deaa7975618dadff0c32535295d3f0d5f577552229ffc
- 28d7e6fe31dc00f82cb032ba29aad6429837ba5efb83c2ce4d31d565896e1169
- 0c6f444c6940a3688ffc6f8b9d5774c032e3551ebbccb64e4280ae7fc1fac479
- f8c08d00ff6e8c6adb1a93cd133b19302d0b651afd73ccb54e3b6ac6c60d99c6
- 731adcf2d7fb61a8335e23dbee2436249e5d5753977ec465754c6b699e9bf161
- 59868f4b346bd401e067380cac69080709c86e06fae219bfb5bc17605a71ab3f
- 3d7cf20ca6476e14e0a026f9bdd8ff1f26995cdc5854c3adb41a6135ef11ba83
- 7e363b5f1ba373782261713fa99e8bbc35ddda97e48799c4eb28f17989da8d8e
- cefea76dfdbb48cfe1a3db2c8df34e898e29bec9b2c13e79ef40655c637833ae
Supporting Documentation
Dealing with cyber threats in the energy sector: Are we on the right path? - Help Net Security
End of Year Recap for 2021 (avertium.com)
As hackers take aim at energy companies, mobile phishing surges - SiliconANGLEg
lookout-energy-tr-us.pdf (bfldr.com)
es-idam-nist-sp1800-2a-draft.pdf
BlackCat ransomware claims attack on European gas pipeline (bleepingcomputer.com)
Npower withdraws mobile app after hackers steal personal details | RWE npower | The Guardian
Mobile phishing attacks targeting energy sector surge by 161% (bleepingcomputer.com)
US reveals Russian supply chain attack on energy sector • The Register
The Top 5 Cyber Threats Within the Manufacturing Industry (avertium.com)
2021 Trends show increased globalised threat of ransomware.pdf (ncsc.gov.uk)
gh-150-wp-energy-sector-cybersecurity-challenges.pdf (guidehouse.com)
Is the Energy Sector Paving the Way or Lagging Behind? - Security Boulevard
Cyber-security incident at US power grid entity linked to unpatched firewalls | ZDNET
Ragnar Locker Ransomware: Everything You Need To Know (Attacks & Analysis) (avertium.com)
Why Energy and Utility Companies Must Beef Up Identity Access Management | BizTech Magazine
161% surge in mobile phishing pushes energy industry to its limits | IT PRO
North Korean Lazarus hackers take aim at U.S. energy providers (bleepingcomputer.com)
BlackCat ransomware claims attack on Italian energy agency (bleepingcomputer.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.